Original link: https://hin.cool/posts/cdncc2.html
cause
Today is the first day of October 2022. I went to bed early last night because I was so sleepy. Woke up at 6:00 this morning (damn biological clock), sat in bed for a while, the sunrise was very beautiful, and then I saw two text messages and found that my CDN was swiped again – one less than the last time A month is a full year.
Turn on the computer and board the console, and find that there are two subdomains that have been swiped, one is the reverse generation jsdelivr, and the other is cloud storage for storing static resources. I set the traffic caps of 5GB and 10GB for the two domain names respectively within 24 hours, one resolves back to the source, and the other suspends the service. However, the console shows that the total amount of swiped traffic is 140GB. It is estimated that the cap has been triggered within an hour since about one o’clock in the morning, and no new traffic will be generated.
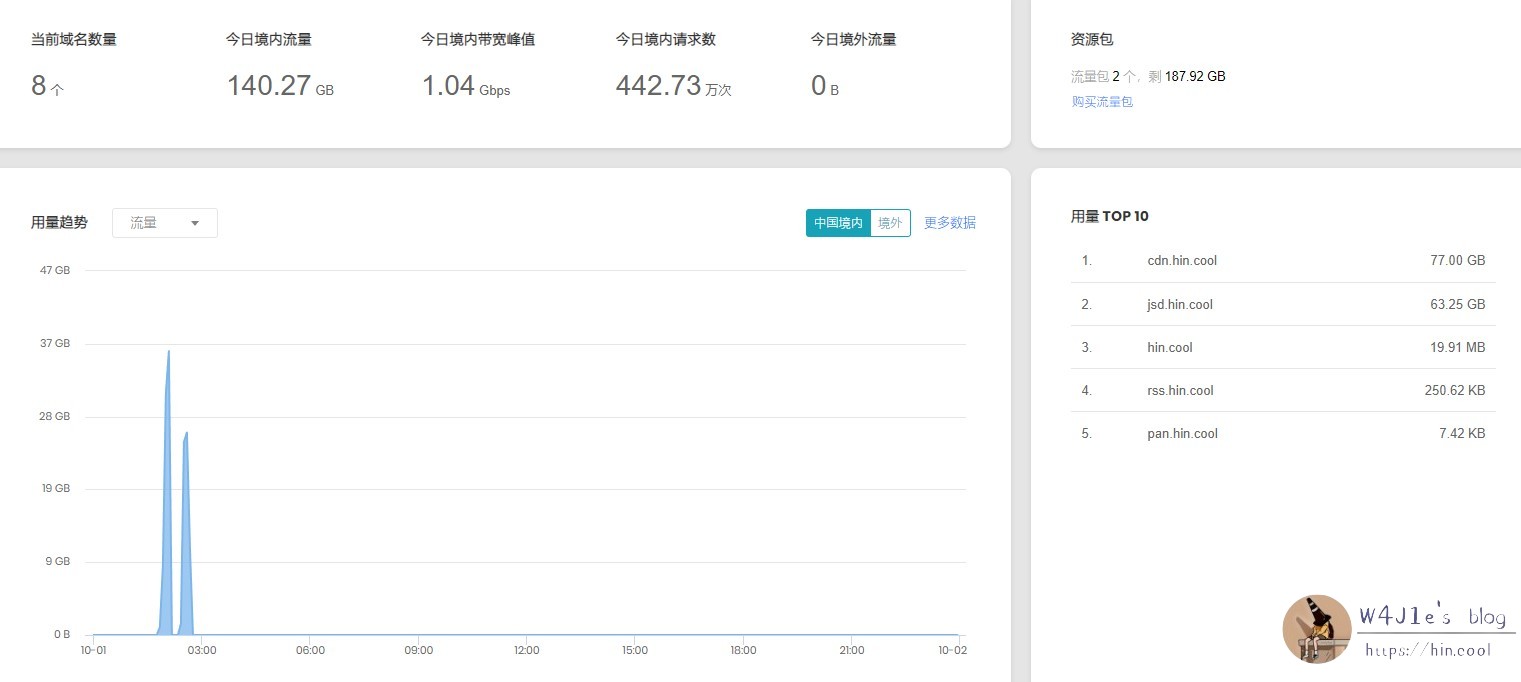
deal with
After confirming that it was swiped, I tried to restart the deactivated acceleration domain name, but it was automatically deactivated soon after. I thought that the attack was still going on, but after trying it twice, I suddenly thought that the cap must be modified in addition to restarting to avoid triggering again.
But I didn’t want to toss anymore, so I resolved the domain name of the reverse generation jsdelivr to Yundun. Duojiyun’s cloud storage can’t be packaged and downloaded, so I couldn’t temporarily transfer the files to the server. After thinking for a while, I thought that after parsing to Yundun, I still use cloud storage as the source station, although these two guys are not from the same family.
At more than seven o’clock, after the analysis was done again, the blog resumed normal access.
detail
The people who brushed my traffic this time are obviously much smarter than the last time. The guy who swiped my traffic last year used Python to keep requesting swipe, so I later banned some abnormal UA requests. This guy has the following characteristics:
1. The source of the attack is not in China, mainly an ip of Amazon Cloud in Tokyo: 13.114.54.145 ;
2. The attacker still chooses the image of the static resource to start, and the reverse generation jsd is a css file of Twikoo;
3. The attacker actually knows to disguise normal UA to simulate access, including but not limited to normal browser UA and Bing crawler:
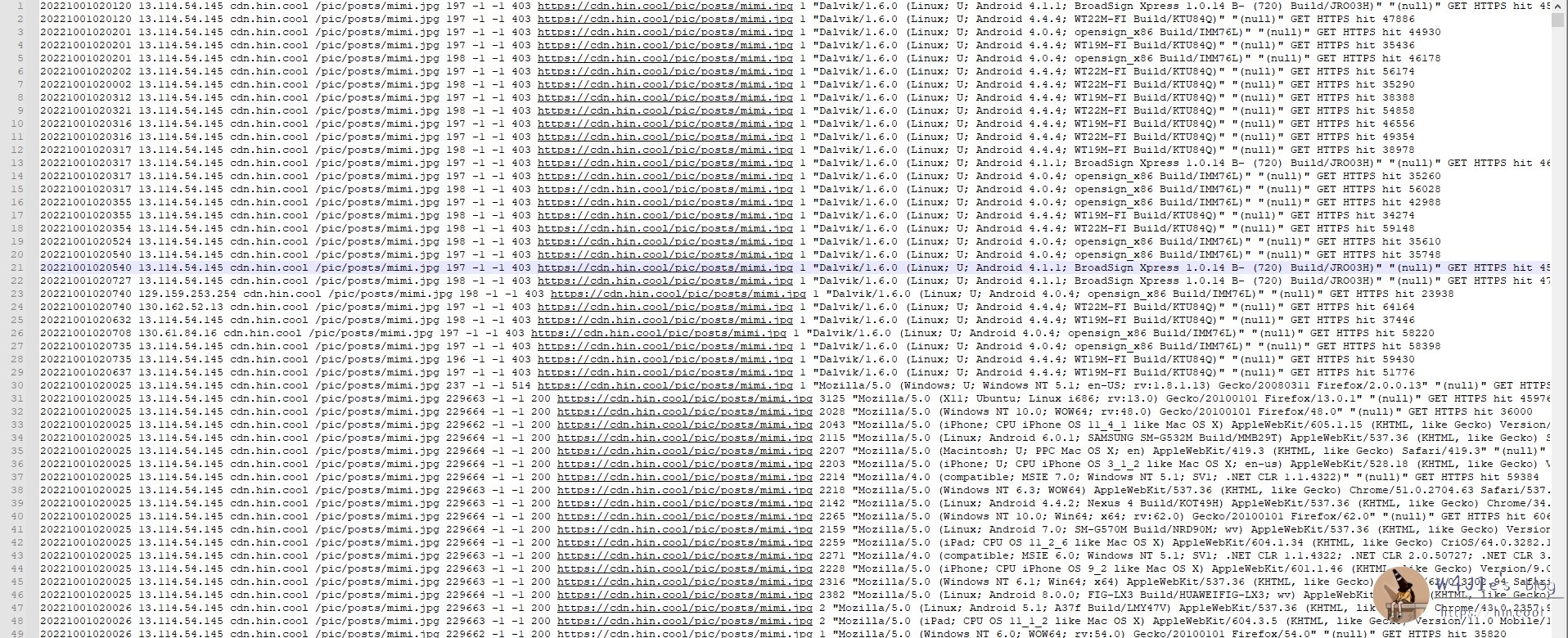
4. The attack suspect visited my blog several times during the period to find the target and check the effect of the attack:
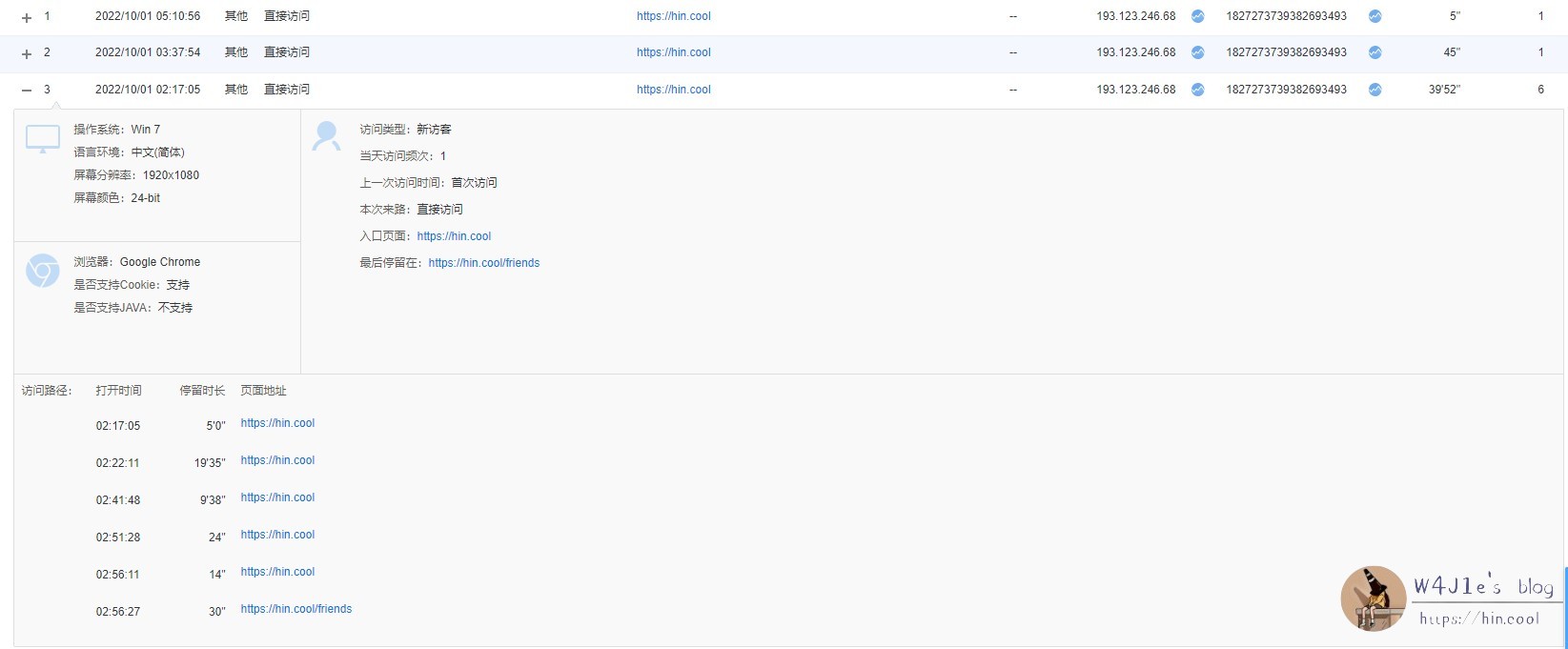
Based on the above information, I guess that a boring person in China used an agent or a broiler for CC. It is difficult to trace the source of this situation, and I don’t want to toss it.
follow-up
After the migration analysis, 15 cc attacks intercepted by waf were found. Because they have been intercepted, the traffic is normal. I reported the situation to Duojiyun, but the other party has not responded further.
at last
I don’t know the reason for the flashing this time. Although I doubted at first whether it was because I temporarily turned on the “allow source is empty access” of the cdn yesterday, but after thinking about it carefully, it should not be a blind cat encountering a dead mouse. , but premeditated, because the sub-domain name of the reverse generation jsd does not have this function enabled, not to mention that the other party will simulate a normal client to request.
The loss this time is almost zero, because the data package I bought for 12 yuan last year has not been used up yet. If it is not brushed, it is estimated that it will be cleared by expiration. Under normal circumstances, my blog only has more than 100 IPs a day, and the traffic is around 400 to 500 megabytes. Therefore, compared to the last time I was brushed 1TB and directly owed more than 400, I am not at all distressed by this attack.
Finally, I want to say to the attacker (if he will also return to the “site” to see my response): The traffic packet has not been flushed, can you do it, TMD, have you not eaten? Can you increase it? strength? !
This article is reprinted from: https://hin.cool/posts/cdncc2.html
This site is for inclusion only, and the copyright belongs to the original author.