Original link: https://oldj.net/article/2023/08/01/code-signing-with-electron-on-windows-2/
Last year, I wrote an article on Electron’s code signing under Windows . In mid-July this year, this certificate is about to expire. I plan to renew it. It turns out that no new pure digital code signing certificates are issued anymore. To perform code signing, you must Buy the version with USB-Shield hardware. Compared with the original digital version, the USB-shield version is much more expensive, and because the USB-shield needs to be mailed, additional postage is required, and it takes a lot more time than the digital version.
The use of the USB-Shield certificate is somewhat different from that of a pure digital certificate, and the main process is recorded below.
purchase certificate
I won’t go into details about the purchase process. There are many service providers, such as DigiCert, Sectigo, SSL.com, CheapSSLSecurity, etc. Of course, you can also find an agent on Taobao.
I purchased the Sectigo certificate through a Taobao agent, because it is the most cost-effective in comparison. The certificate was officially sent from Canada by Sectigo. When I placed the order, it took 21 days for the shipment to be delivered because the manufacturer’s chips were out of stock.
The picture below is what the USB shield I received looks like.

Preparation
Since my main development machine is a MacBook Pro with an M1 chip, I hope to use this U-shield directly on the mac instead of changing computers when packing and signing. After some exploration, it is found that it can be achieved. The main points are as follows:
- Install Parallels Desktop Professional Edition on macOS
- Install Windows 11 for Arm in Parallels
- The USB-Shield needs to be connected with Windows 11 in Parallels, not with macOS
Next, you need to install the SafeNet Authentication Client (SAC) software on Windows 11 in the virtual machine. You can usually find the download link from the certificate issuer’s website or in your email.
After installation, plug in the USB shield, if you see your device in the SAC software, it means everything is normal, as shown in the figure below.
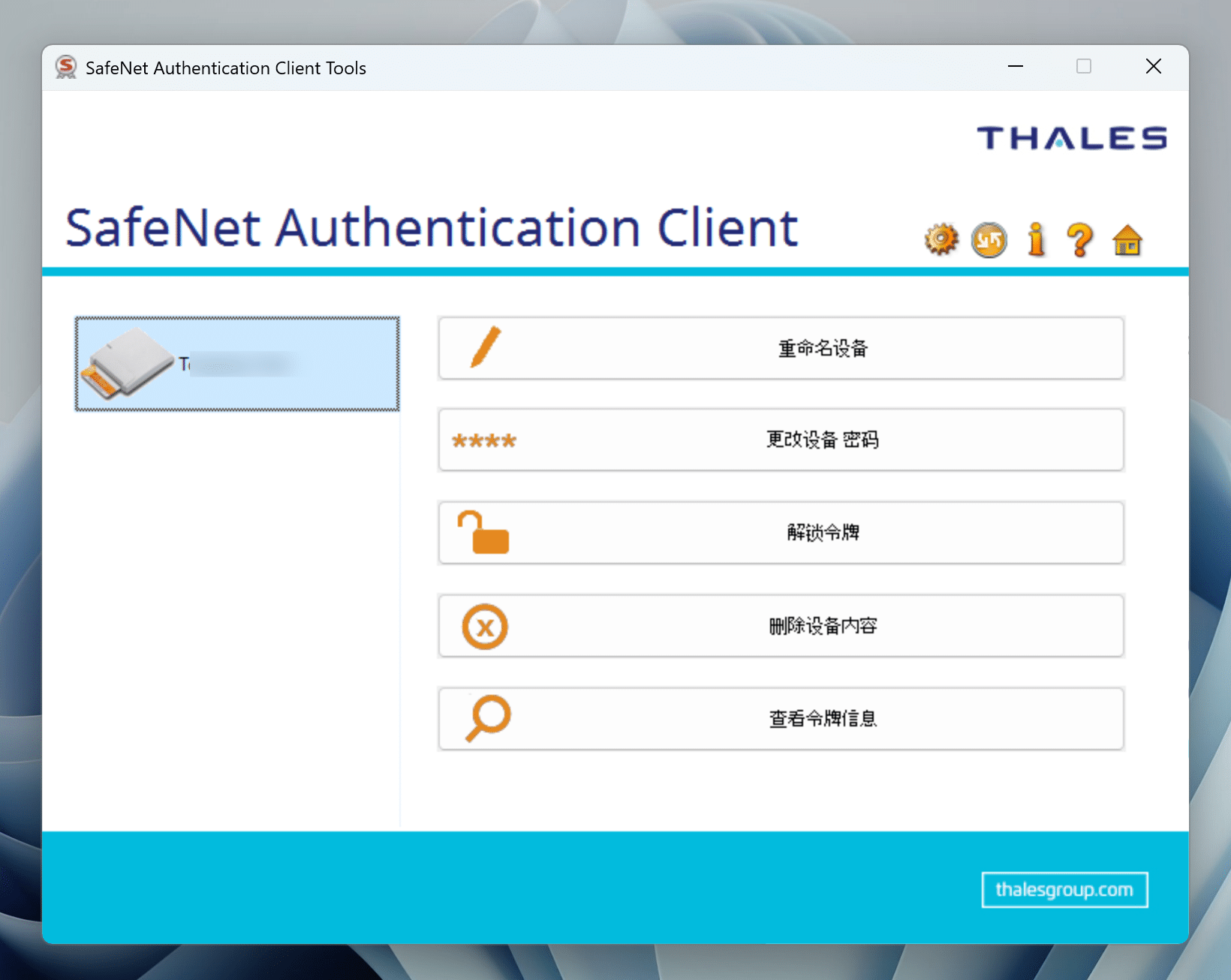
The email sent by the certificate issuer contains the initial password, which can be changed in this software. Be careful to keep the new password well, it will be troublesome if it is lost accidentally.
install certificate
Next, this certificate needs to be installed into the current Windows system.
Click Advanced View in the SAC interface:
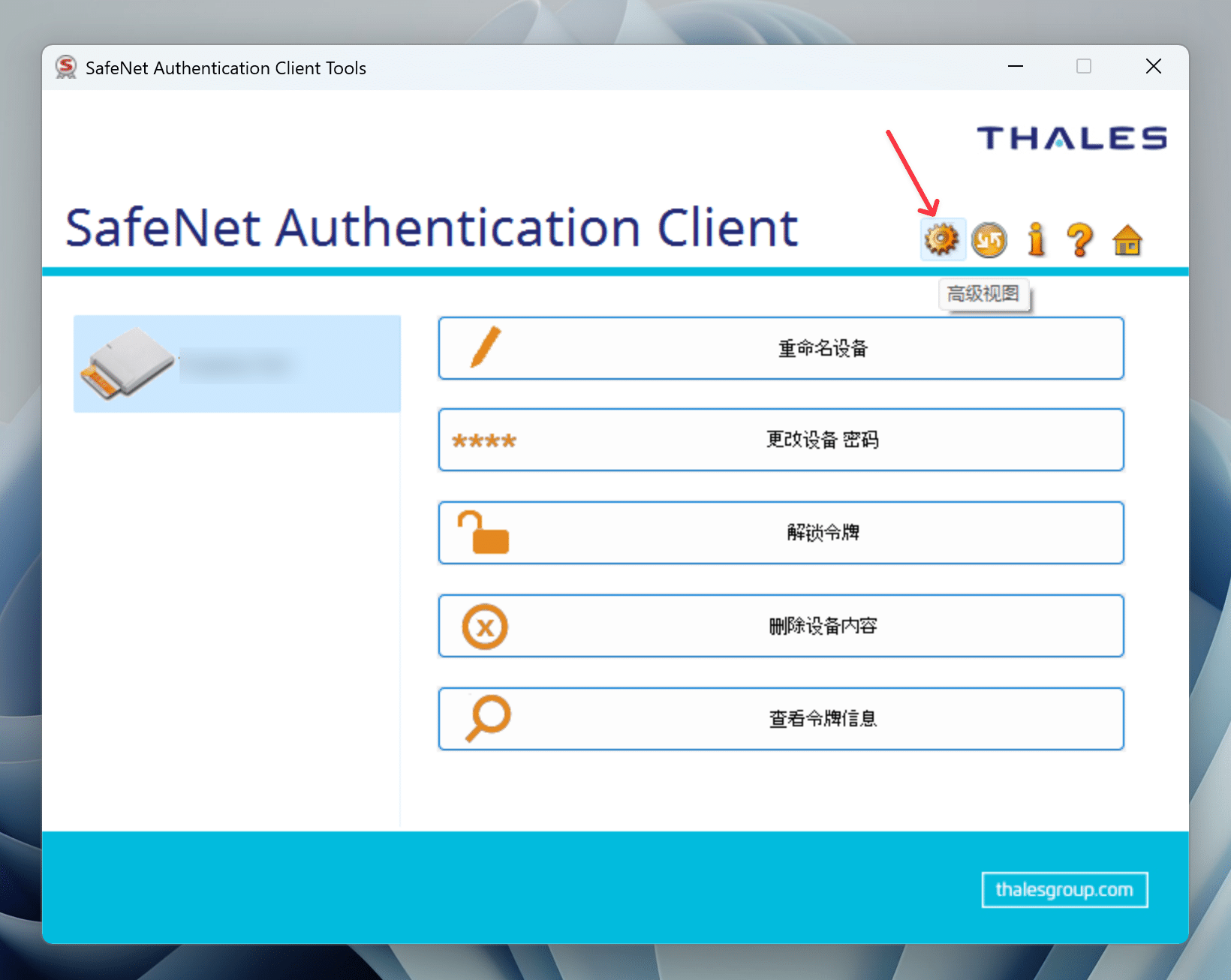
Find the certificate and double-click to install it, as shown in the following figure:
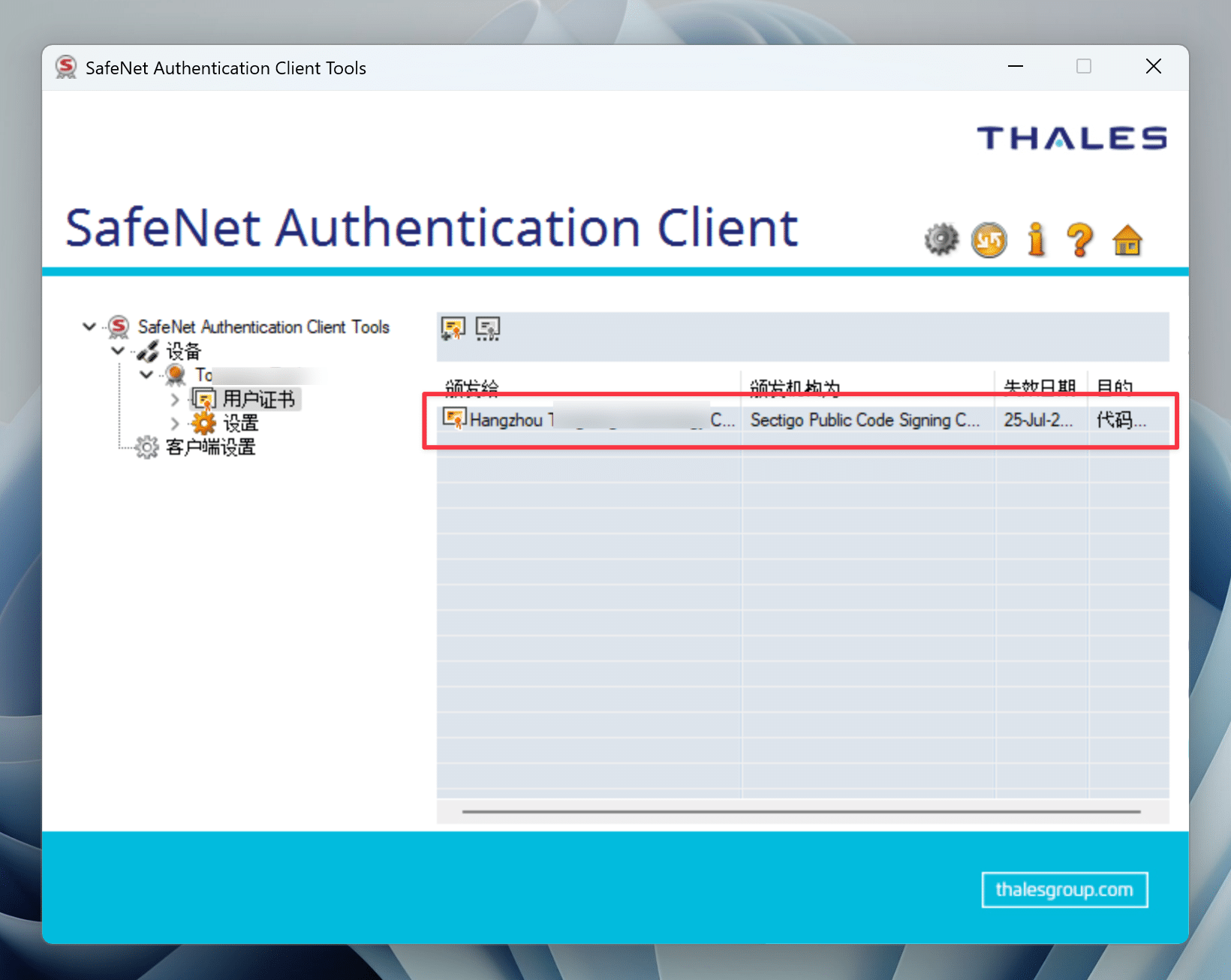
In addition, the SAC software also has a macOS version, but this certificate does not seem to be installed on macOS. Even if it is installed, it should be useless, because the certificate in Windows will still be called when signing later.
Used in Electron
I use electron-builder for packaging and signing. The main library and version number are as follows:
The key configuration of electron-builder is as follows:
win: { // ... verifyUpdateCodeSignature: true, signingHashAlgorithms: ['sha256'], signAndEditExecutable: true, signDlls: false, certificateSubjectName: 'YOUR_NAME', publisherName: 'YOUR_NAME', rfc3161TimeStampServer: 'http://timestamp.sectigo.com', timeStampServer: 'http://timestamp.sectigo.com', },
Replace YOUR_NAME with the name in your certificate.
problem solving
During the signing process, I encountered the following error:
ensure that 'Share folders' is set to 'All Disks', see https://goo.gl/E6XphP Error: Exit code: 2. Command failed: prlctl exec {e28c7c00-0805-4729-91e9-3bfeacdbbbf8} --current-user \\Mac\Host\\Users\wu\Library\Caches\electron-builder\winCodeSign\winCodeSign-2.6.0\windows-10\arm64\signtool.exe sign /tr http://timestamp.digicert.com /sha1 C2F9D1106A2D69E9351CCE1EF1B6E1AA3E9C475B /s My /fd sha256 /td sha256 /d ......
After researching for a while, I found out that my mac has an M1 chip, and the installed Windows 11 virtual machine is also of the Arm version, and the winCodeSign tool does not provide the signing tool of the Arm version, so the command fails.
The solution is very simple, navigate to ~/Library/Caches/electron-builder/winCodeSign/winCodeSign-2.6.0/windows-10/ directory of mac, copy the x64 directory, and rename it to arm64 .
Next, you should be able to sign the exe file of Electron smoothly.
Improve
Although the signature can be successfully completed, the password input box will appear many times during the process, as shown in the following figure:
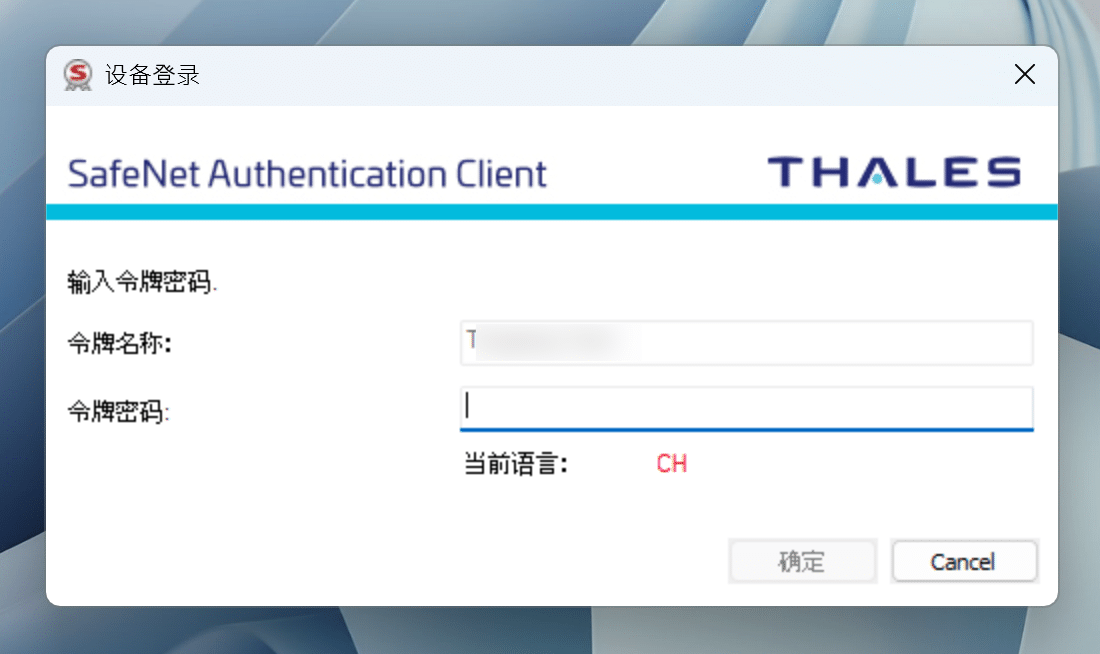
This password input process is not only cumbersome, but also prevents the command from being completed automatically, because the process will be stuck every time and the password needs to be entered manually.
It stands to reason that there should be a more elegant approach in this place. The documentation of electron-builder also mentions parameters such as certificatePassword and CSC_KEY_PASSWORD , but I have tried many times but it still cannot take effect.
In the end, I wrote a simple AHK script that solved the problem. The script content is as follows:
Loop { If WinExist("设备登录", "令牌密码") { WinActivate Sleep 500 Send "{Raw}YOUR_PASSWORD" Send "{Enter}" } Sleep 1000 }
Be careful to replace YOUR_PASSWORD with your password. Of course, you can also save the password in an environment variable, and then read it from the environment variable in the AHK script.
summary
The purchase and use of USB-shield code signing certificates are more troublesome than previous digital certificates, but in order to improve the experience and security of users downloading and installing software, this certificate is still worthwhile.
This signing certificate needs to be installed on Windows, but a Parallels virtual machine on macOS will also work.
For some related matters, you can also see the usage of digital certificates I wrote a year ago.
This article is transferred from: https://oldj.net/article/2023/08/01/code-signing-with-electron-on-windows-2/
This site is only for collection, and the copyright belongs to the original author.