Original link: https://www.baifan97.cn/archives/1222/
00 Introduction
In the Internet age, as long as you are using any product on the Internet: your information is fully transparent
This article might scare you, but don’t
Know it first, understand its root, in order to better prevent this kind of thing from happening
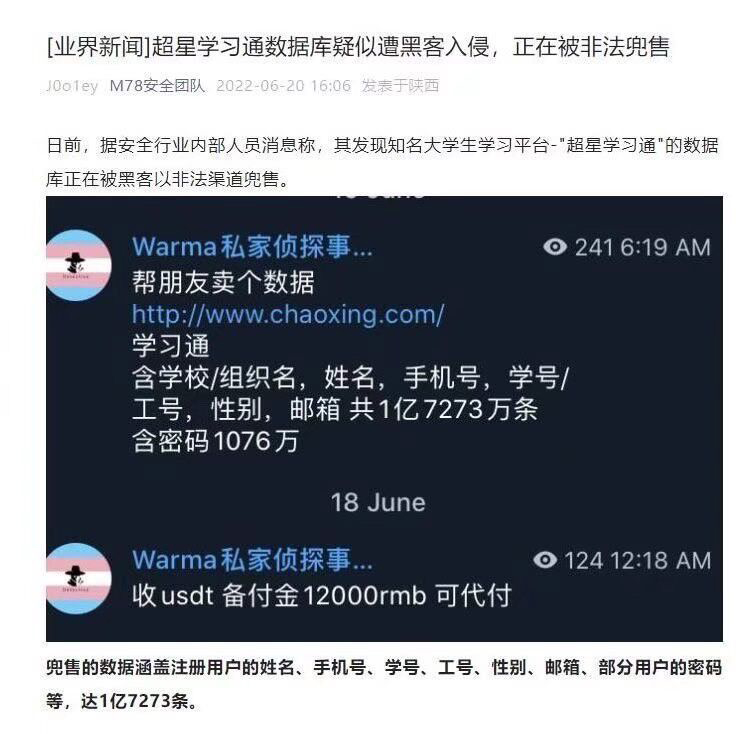
Superstar Learning Pass database leak
On June 20, 2022, the Chaoxing Xuetong database was leaked and illegally sold in the social worker group, including user names, mobile phone numbers, student numbers, job numbers, gender, email addresses, and passwords of some users, reaching 17,273 items. Among them, there are 1076 passwords.
The password encryption method is base64, which can be easily converted into plain text.
About 10 million of them are college teachers on the job, and the remaining tens of millions are college students who have graduated or are currently studying, including students and teachers in police academies.
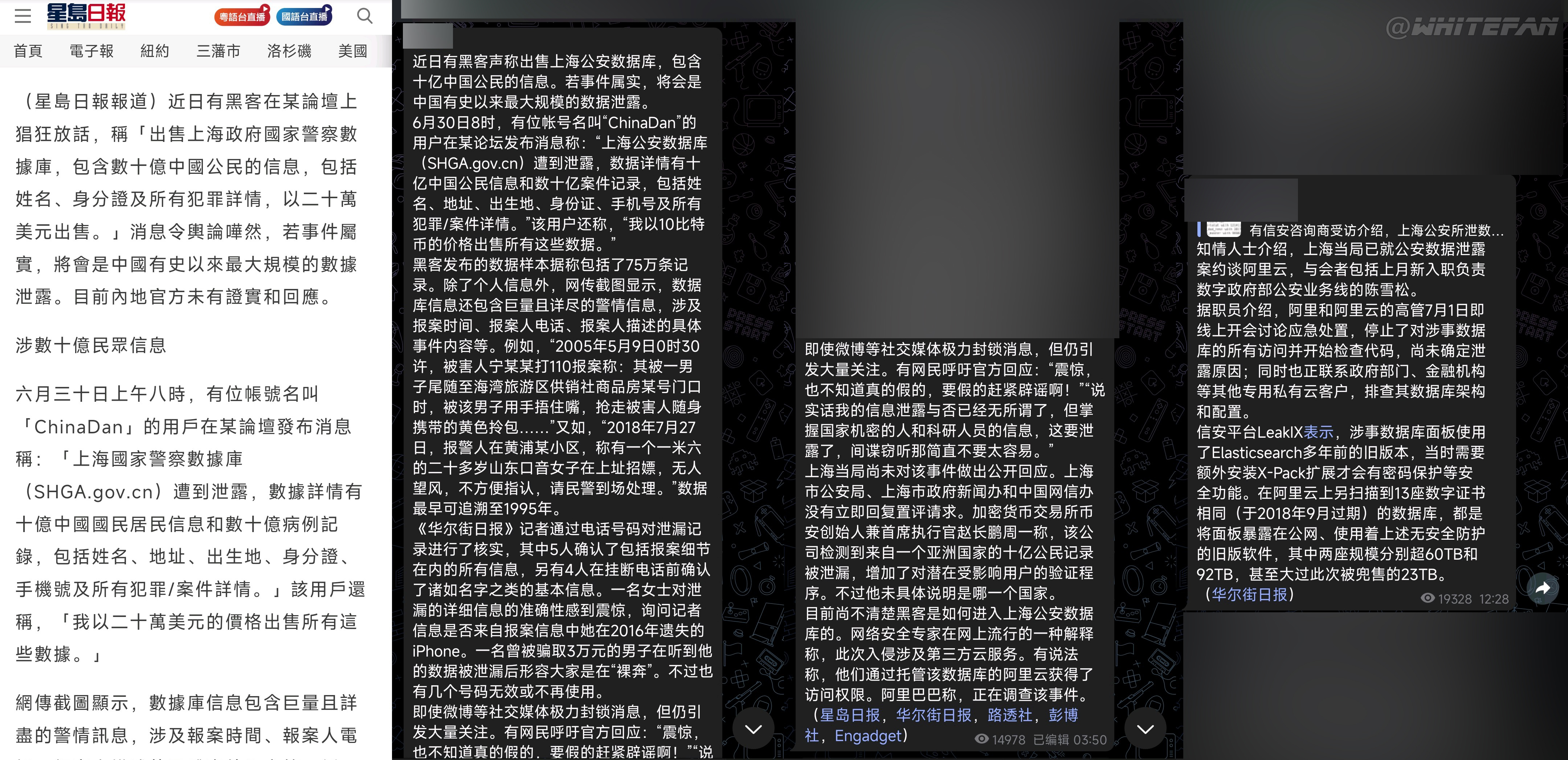
Shanghai State Police database leaked
On July 6, 2022, the Shanghai National Police database was leaked, containing information on 1 billion Chinese citizens and police records. Including name, address, ID number, place of origin, mobile phone number, case report and police dispatch information, political identity, occupation, government medical records, shopping information, military service information, illegal records and other information, through the analysis of the two released data samples Look at it, basically confirm the authenticity of the data.
Henan National Police Database Leaked
On July 7, 2022, the Shanghai National Police database was leaked, containing the information of 90 million citizens. Including name, age, address, ID card number, mobile phone number and other information, by analyzing the 40,000 data samples that have been released, the authenticity of the data can be basically determined.
Shanghai Suishenma Data Leakage 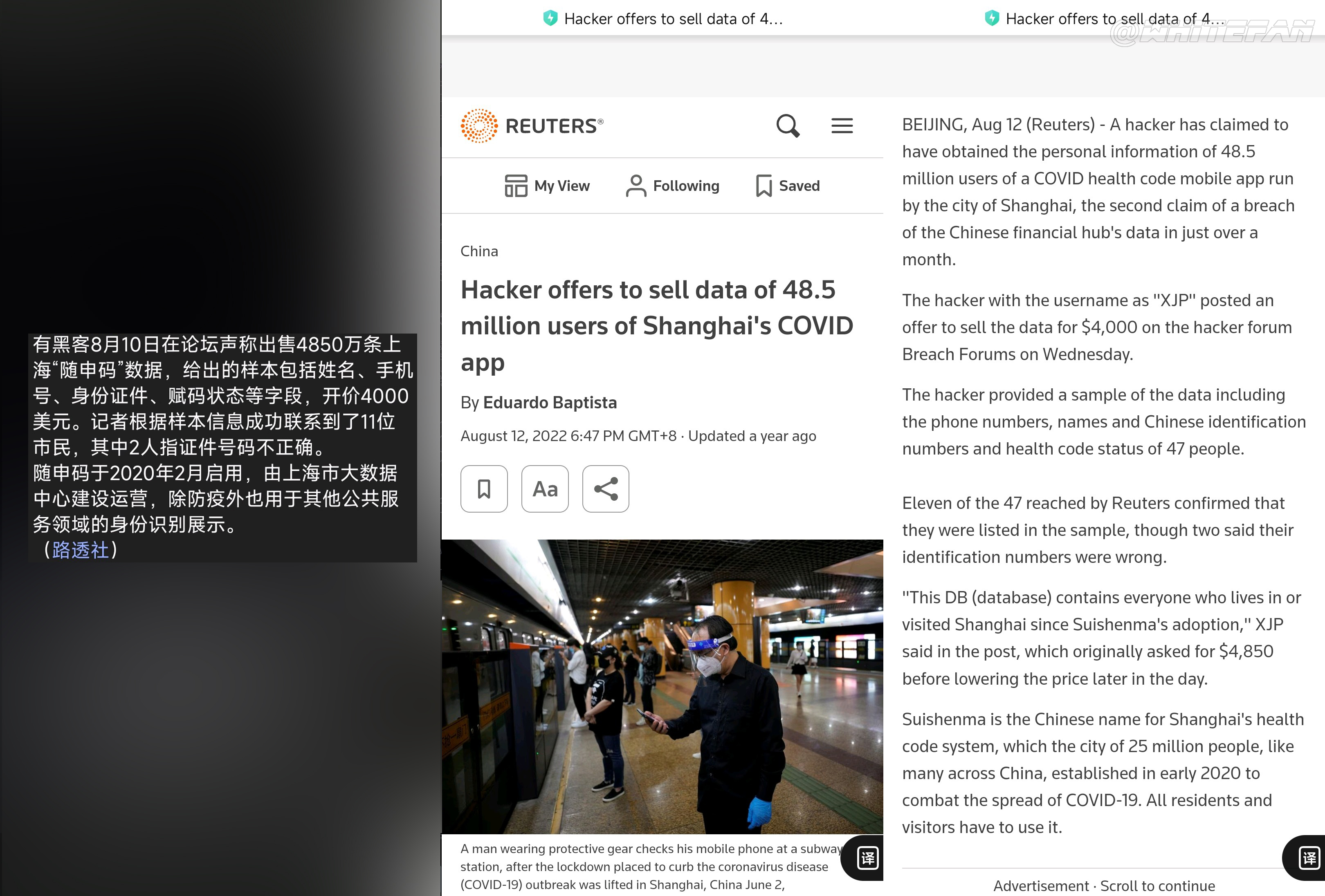
Data of 500 million Weibo users leaked 
First of all, data leaks not only happen at home, but even more abroad
Secondly, data leaks have happened a long time ago and are very common. Information leaks on QQ and Weibo have happened many times
It’s just that the scope of the data leak is wider this time, and it has attracted enough attention in China
Looking at it now a year later, in fact, these incidents have not enhanced our security awareness 
01 How much information has been leaked?
As long as you have a mobile phone number, you can find at least 30% of the information about you. If you pay a certain fee, you can get more information: including QQ numbers (some with previously used passwords and QQ groups you have joined), Weibo numbers , ID number, education information, ID card photo (probably about 14-20 years old), bank card number, online shopping records (including purchase time, item name, recipient, user name, address), other people’s communication A note to myself in the record…
Does it sound unbelievable, but this is the by-product of the real-name system we have implemented for more than ten years 
Self-examination, what did the human flesh find out?
How much information can I find out if I use my mobile phone number to kill myself? 
I sent my mobile phone number to the order robot, and it took only a few seconds to send a message: QQ, Weibo, Tieba, address book notes 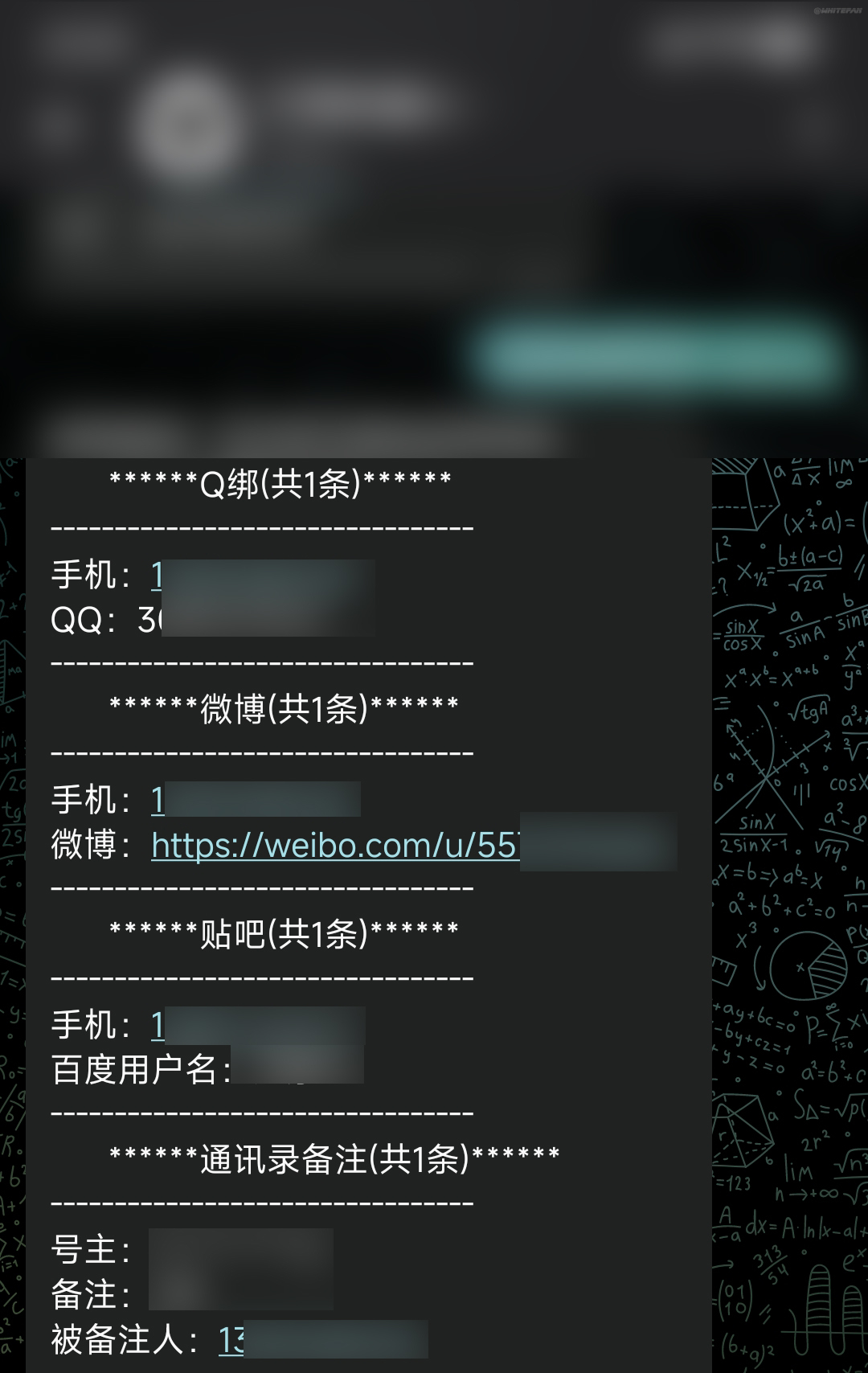
After the payment is completed, the asterisk content also becomes visible content 
Then I found my shopping information (including Jingdong, Taobao)
Sensitive information has been processed, and the asterisk content in the picture requires payment to view
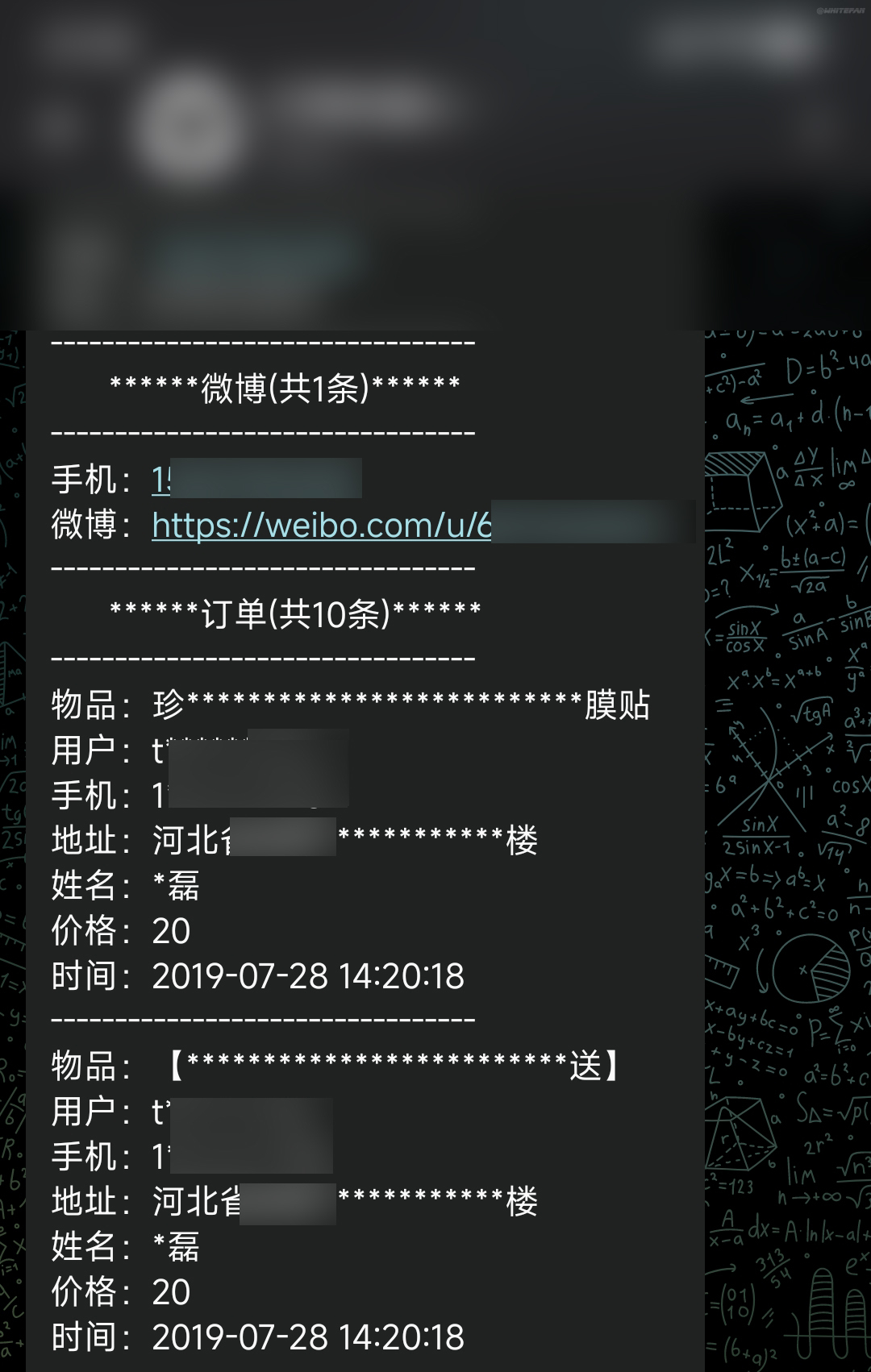
When I open my Taobao, the time and shopping items are right (fortunately, my shopping recipients hardly use their real names) 
There are also some orders from JD.com
So far, we still can’t tell where the source of the leak comes from: Is it the JD.com/Taobao official? Or a seller? Or courier?
The price of obtaining an ID card will be higher than before, and at the same time, you can find the school information of Xuetong 
A few months ago, a certain channel announced an interface for querying ID card headshots. I tested it several times, and it should be a photo of the ID card 5 years ago.
大头接口json 版本(真实链接已做处理):https://www.dra*****soul.cn/api.php?act=photo_json&idname=姓名&idcard=身份证号That is to say, as long as you have a person’s name and ID number, you can get the electronic version of the photo on the person’s ID card, even if you don’t have an electronic version of the photo on the ID card 
Among us, the most common leaks are: QQ account (1.6 billion data leaked), Weibo (500 million data leaked), education information including ID number (nearly 200 million super star database leaked)
And more data is being sold on the dark web at a price 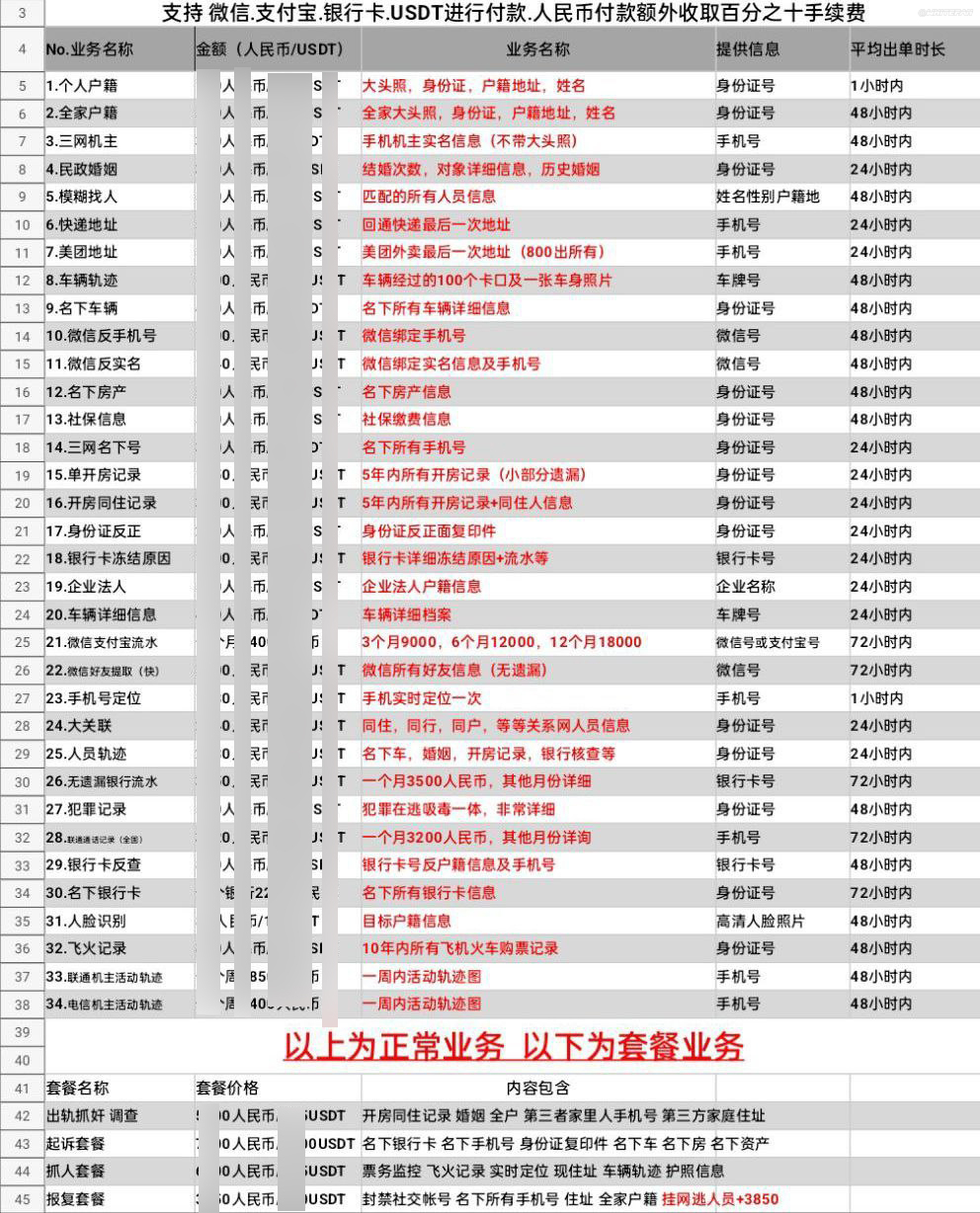
Simple data can be automatically queried by robots, while complex information requires manual operation
Among the statistics available, these channels have already attracted more than 300,000 users. It can be seen that this black industrial chain has developed relatively well. 
02 Dig the source of information leakage
Out of Control App Permissions
Any APP wants to get more permissions on your mobile phone, ranging from storage, reading and writing permissions, to reading contacts…
It is big enough to bind a mobile phone number, or even an ID number for real-name authentication and face authentication
And after we open these apps for the first time and press the同意button, the information will be given to them as a matter of course to use these apps. Whether there is a perfect process to protect our information is unknown
greedy human nature
Through the following pictures from civil aviation security checks, railway station gates, provincial permanent resident population databases, hotel scene pictures, etc., we can see how serious the information leakage has become
 Mobile phone positioning
Mobile phone positioning 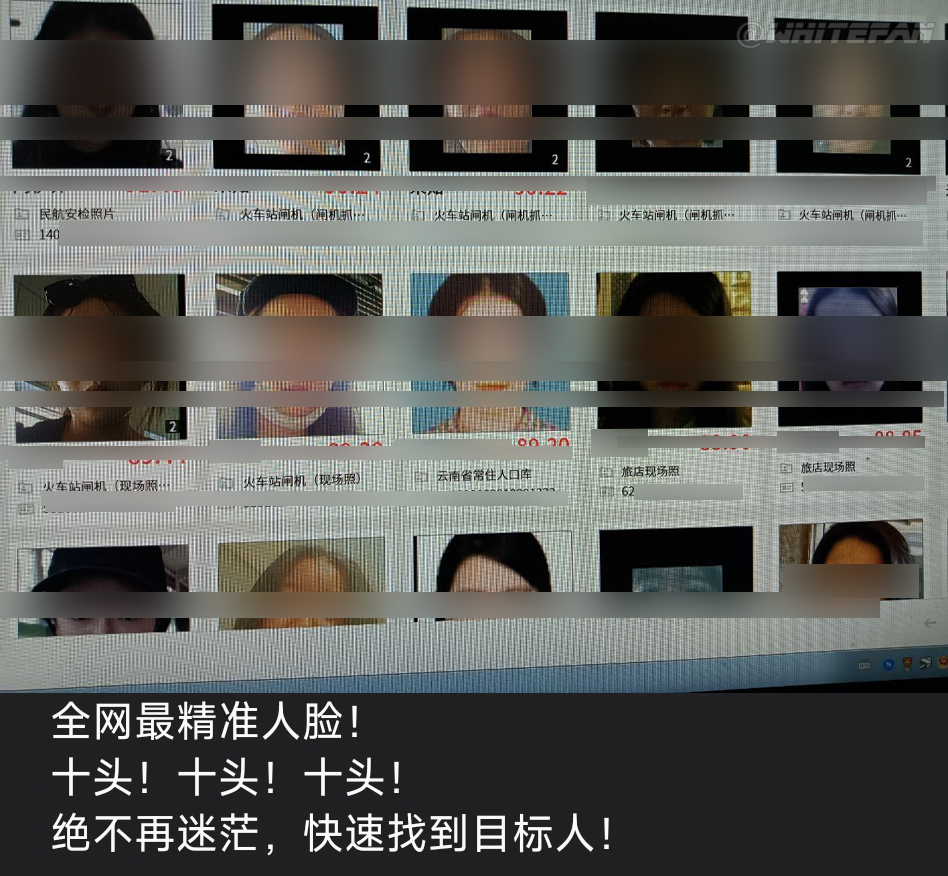 Face authentication photo
Face authentication photo  open house record
open house record  Social Security Information
Social Security Information Is this data really stolen by hackers?
I am more inclined to be social workers/insiders/related technical personnel to intentionally leak
In the dark web, the most information they collect data is to find some insiders who have data to cooperate and exchange benefits. Obviously, this is very efficient, and the authenticity and validity of the data is higher. 
03 How to protect personal information
In the current Internet environment, it is almost impossible to achieve no data leakage.
The premise of obtaining all your information, in fact, only need to master one of your information
The mobile phone number is the most used piece of information, and the information involved is huge
 Information that can be obtained by mobile phone number
Information that can be obtained by mobile phone number
Your mobile phone number can also be reverse-checked through other channels. You can check your bound mobile phone number through QQ/WeChat/Weibo/Douyin/…, and you can also find out that the friends who interact with you on social platforms may also be you The mobile phone number left in the car, the mobile phone number filled out unintentionally…all have the opportunity to be used by criminals
Some people may think that this information is of little value. What is the use of my information if they know it?
In fact, a lot of information has been leaked, you have not been targeted because you are worthless~ 
Admittedly, it’s not worth it to get this information from someone who has nothing to do with it
But the Internet is a network that connects all of us. It may be that you registered an account, posted a comment, or got involved in a certain event…
You may be targeted by people with bad intentions and attack you or even your family and friends
There have been many incidents in which people involved in popular incidents have been raped by human flesh and cyberbullying.
Similarly, criminal gangs will use this information to gain further trust from you and carry out more perfect scams
So for yourself, and for your family and friends, you should try to avoid information leakage
Intentionally obfuscate personal information
To be honest, information leakage is inevitable, and it is not something we can prevent
The total data of Weibo has also been leaked among the 500 million Weibo data, and the ID numbers and mobile phone numbers of many celebrities have also been disclosed on the dark web
What we can do is to let the real information leak less 
The principle is to weaken the connection between different platforms and different aspects of information
for example:
Separate the use of your two mobile phone numbers, one is dedicated to the country/government/school and other relatively safer places, and the other is used on major social networking platforms to avoid using the same ID and the same avatar on different platforms, Try not to use the same mobile phone number to bind the account. The recipient should not use the real name, and occasionally change the delivery address. Don’t specify the building number and house number, as long as it can be delivered: You can choose to fill in the location of the nearby Cainiao Station, JD.com /SF Express can wait until the call to inform the specific location
Now, in addition to WeChat/QQ, short videos such as Douyin are also apps that most people open more than once a day
Douyin has also become a major channel for information leakage  Douyin information query service on the dark web
Douyin information query service on the dark web
Therefore, if the social account does not need to be used by everyone, you can set it as a private account and close some permissions 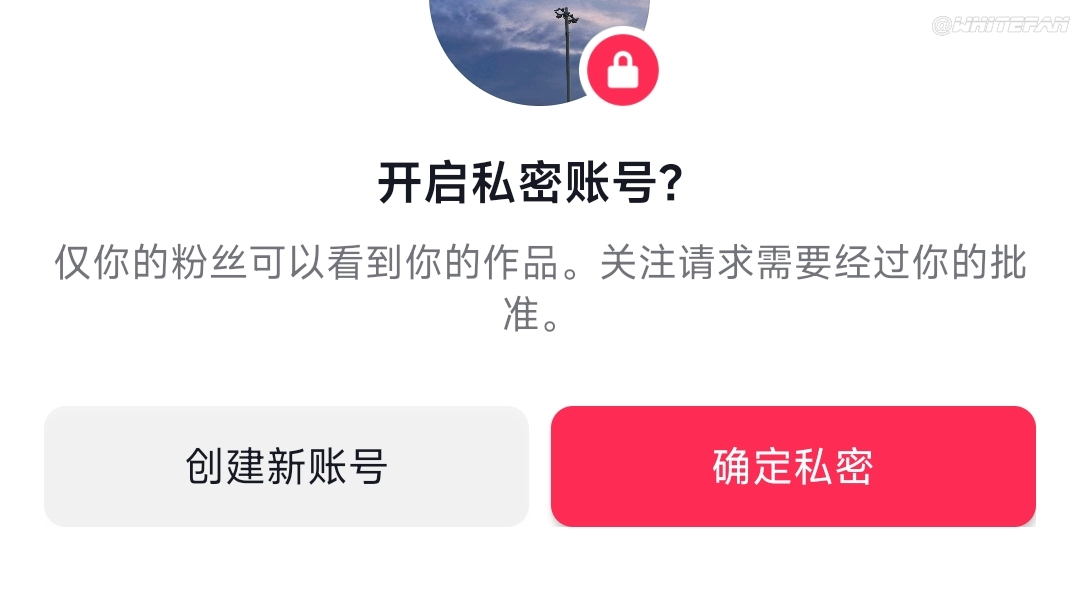 Set as a private account
Set as a private account  Turn off address book lookup
Turn off address book lookup
Do not open the positioning of social platforms at will, and try to ensure that every time you use the permission, open the fuzzy positioning with your permission, and only allow this time to use 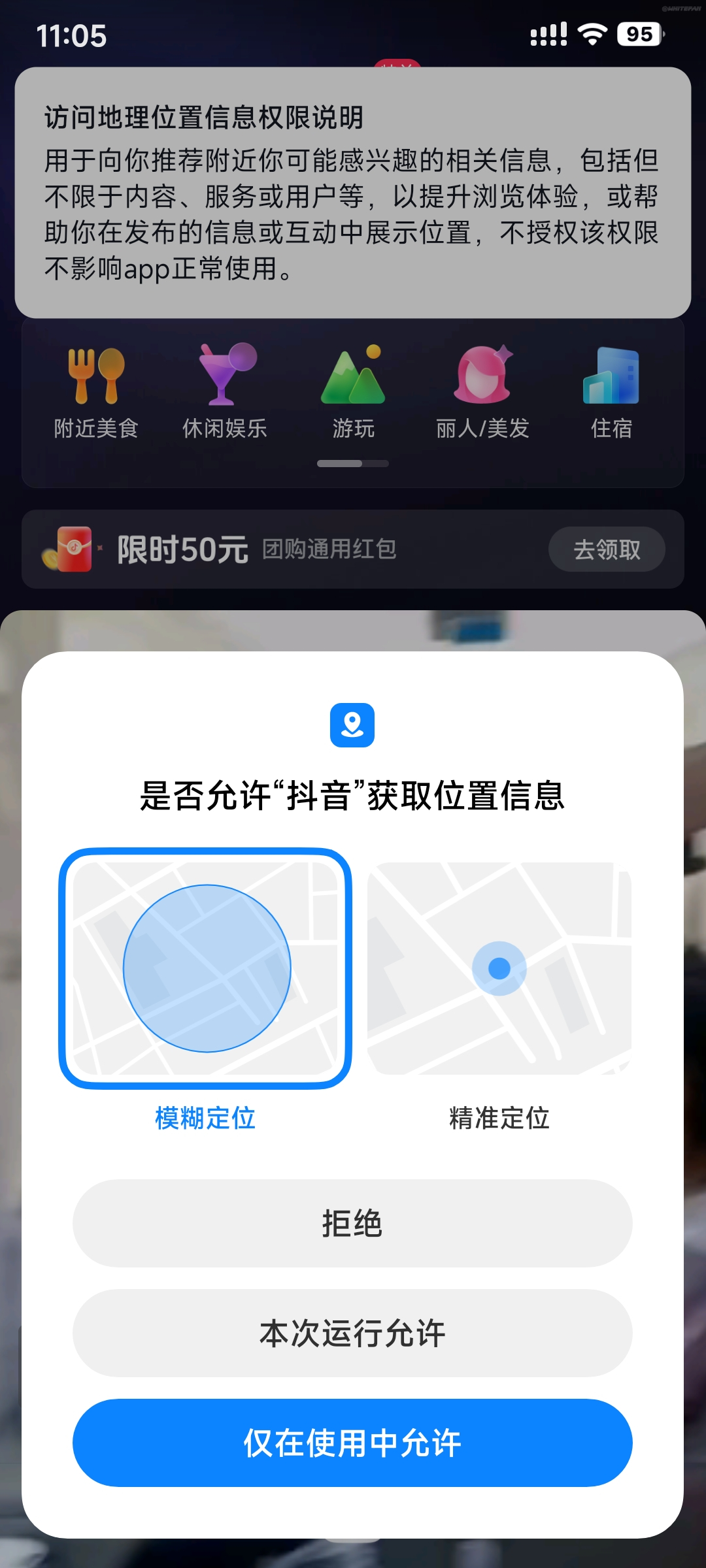 Turn on fuzzy positioning
Turn on fuzzy positioning
Photos sent on social platforms will also reveal a lot of information. It only takes a certain amount of time to deduce the time and place of shooting, so try to think about it before sharing. Maybe a certain photo will plant the seeds for a certain event in the future. 
If you have access to other people’s information, please protect it as much as possible for them
Whether it is school or work statistics, in most cases, to save trouble, everyone will fill in a form together, and everyone can see the information filled by others. Such a large amount of information has actually been made transparent.
So, if you are in charge, should you do something?
END
This article is not to teach you how to human flesh yourself, but to let you understand these and deal with them better
This information may not be threatening to you now, but who knows in the future?

This article is transferred from: https://www.baifan97.cn/archives/1222/
This site is only for collection, and the copyright belongs to the original author.