Original link: https://www.kawabangga.com/posts/5324
Today there is a need like this:
- We provide HTTP services to another team. During joint debugging, the client can only initiate requests from the server;
- We want to deploy the service on a local laptop for debugging, but there are NAT and firewalls between the server and the laptop, and the client on the server can only access the server, not our laptop;
- But our notebook can also be a document server;
This is a typical requirement for intranet penetration. I found out today that socat can do such a thing.
As shown in the figure below: the IP of 5.5.5.5 on the server side can be accessed, but the IP on the laptop cannot.
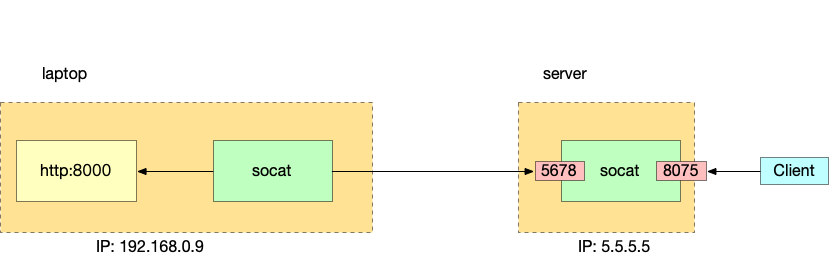 socat intranet penetration principle
socat intranet penetration principle
The idea is:
- We open two socat processes, one on the local notebook and the other on the server side;
- The socat on the Cerver side does one thing: Listen to port
8075Once a connection is established, it starts to listen to port5678, and then copies all the content received by port8075to5678, and copies the content of5678to8075; - The socat on the client side does one thing: keep trying to connect to the address
5.5.5.5:5678. Once the connection can be established, it will establish a connection with192.168.0.9:8000(or127.0.0.1), and then upload the content of5.5.5.5:5678Copy to192.168.0.9:8000, copy the contents of192.168.0.9:8000to5.5.5.5:5678;
The command run by the client is:
socat -d -d -d -v tcp:5.5.5.5:5678,forever,intervall=1,fork,reuseaddr tcp:192.168.0.9:8000
The command run on the server side is:
socat -d -d -d tcp-l:8075, reuseaddr, bind=0.0.0.0, fork tcp-l:5678, bind=0.0.0.0, reuseaddr, retry=10
In this way, the service running locally at 192.168.0.9:8000 is exposed through 5.5.5.5:8075 . When a user accesses 5.5.5.5:8075 , it is the same as accessing 192.168.0.9:8000 :
- The user establishes a TCP connection with
5.5.5.5:8075, and sends the request to5.5.5.5:8075. At this time, it is actually the Socat process on the Server side that receives the HTTP request; - Socat on the server side starts to listen
5.5.5.5:5678; - Socat on the client side keeps trying to connect to
5.5.5.5:5678(according to the above parameters, it tries once every 1s). At this time, because of step (2), the connection between Socat on the client and5.5.5.5:5678is successfully established, so Socat on the client side also established a connection with192.168.0.9:8000; - Socat on the server side sends the HTTP request to Socat on the client side;
- Socat on the client side sends the HTTP request to
192.168.0.9:8000; - When the HTTP Server on the notebook sends the HTTP Response, Socat on the client side sends the HTTP Response to
5.5.5.5:5678, and it is Socat on the server side that receives this response; - Socat on the server side sends the HTTP response to the client;
- Client receives HTTP Response.
refer to:
related articles:
This article is transferred from: https://www.kawabangga.com/posts/5324
This site is only for collection, and the copyright belongs to the original author.