Original link: https://www.ifanr.com/app/1546279
How do I log in to my account without a password? Google gave its solution, pick up the phone, scan the code, and log in successfully. No password is required, and no secondary authentication is required.
Simple operation, but safer.
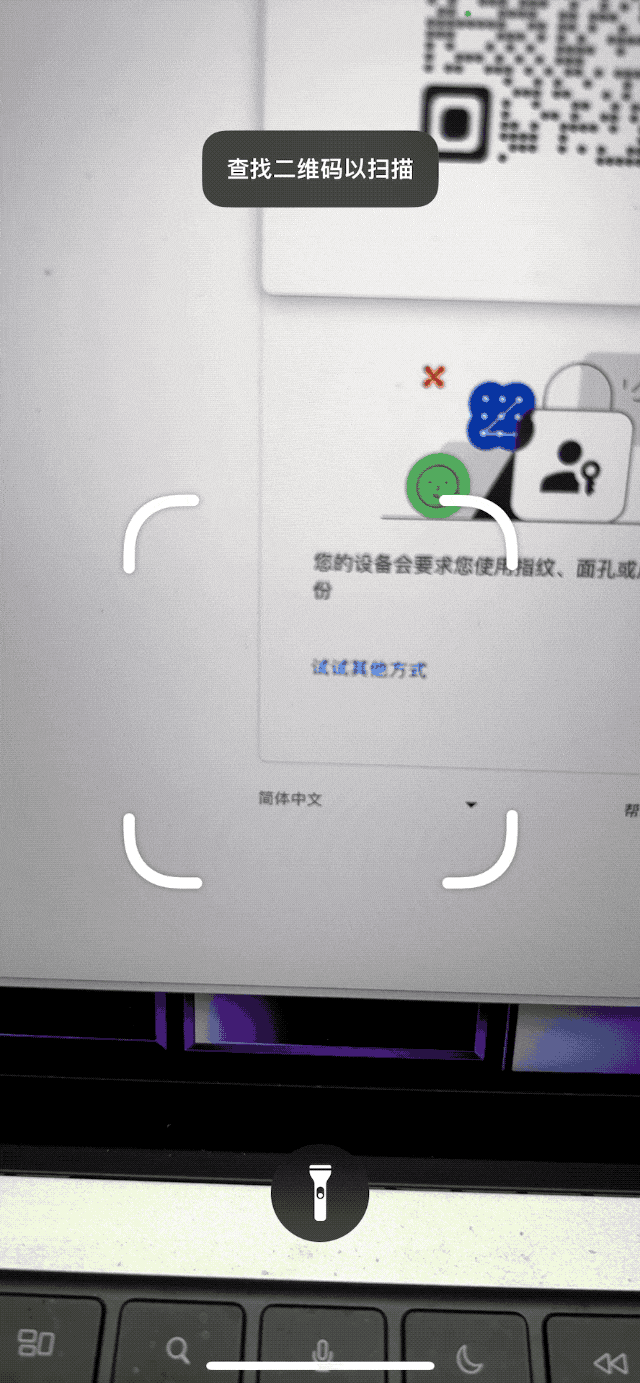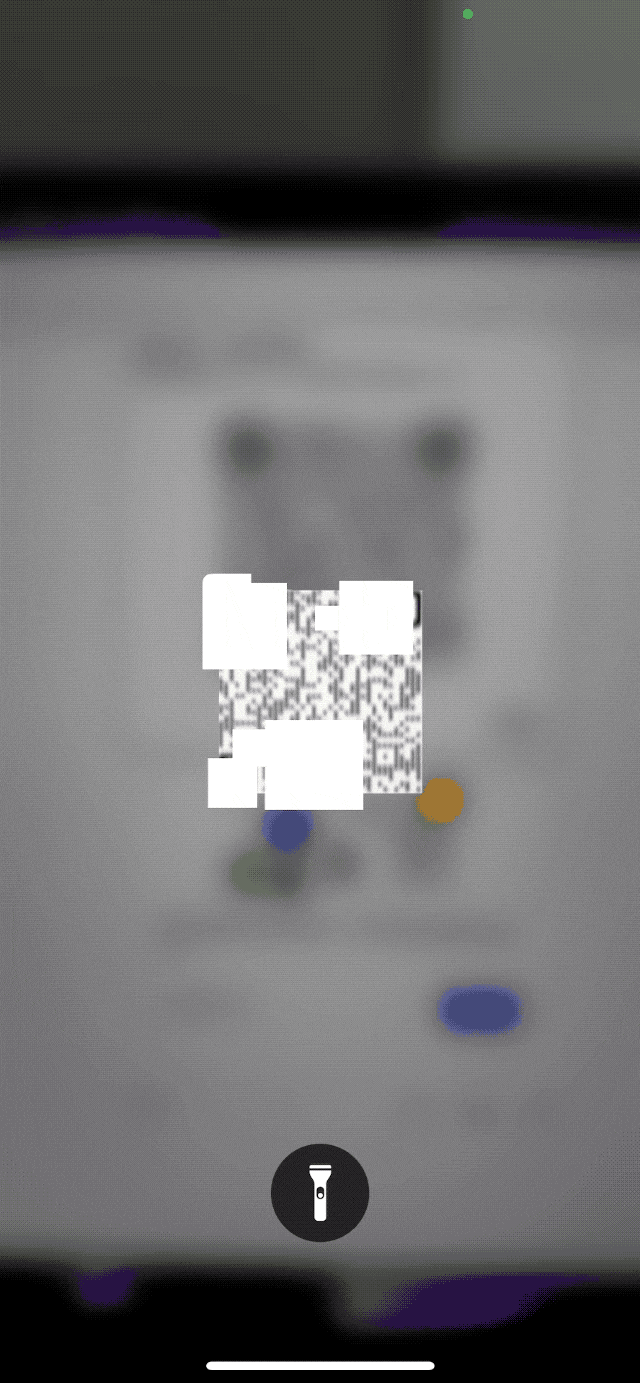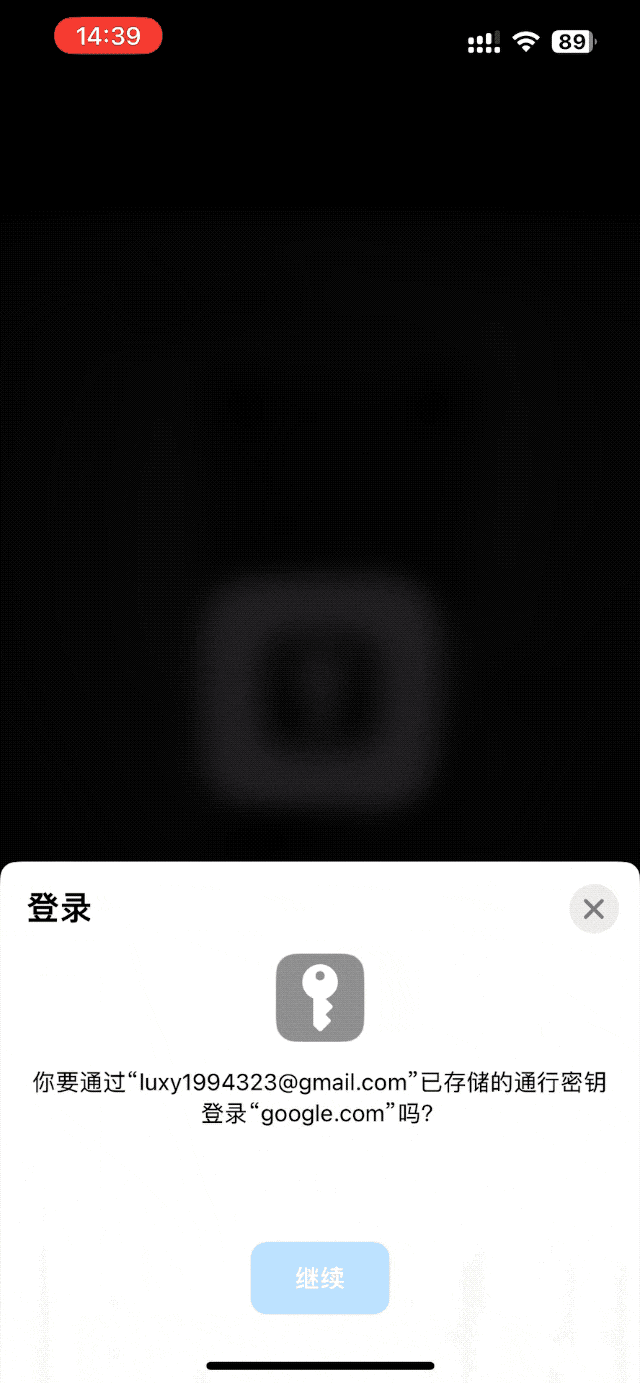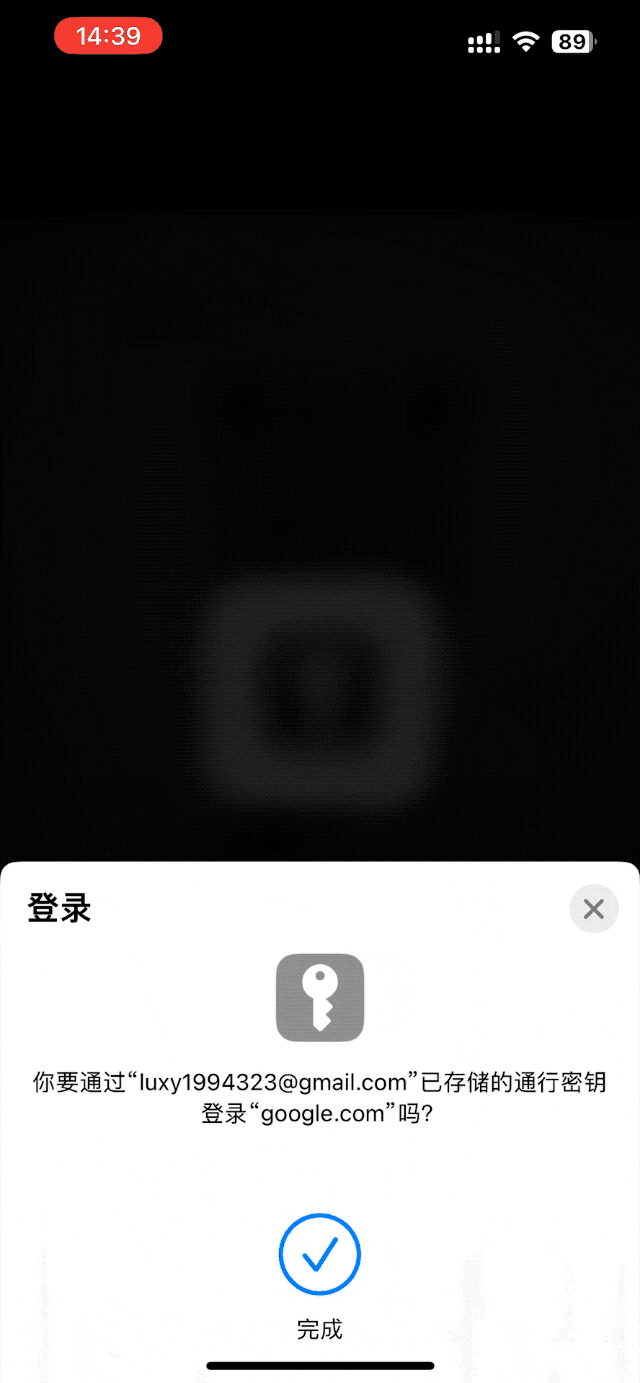
say goodbye to all passwords
Why does this seemingly similar login method to WeChat scan code let us say goodbye to passwords?
First of all, the underlying principles of Google Passkey and WeChat code scanning are completely different. Google Passkey follows the W3C protocol and is completely offline without server participation. Scanning code is only one of its login methods. On a certified device/browser, you You can also log in with your fingerprint or Face ID.
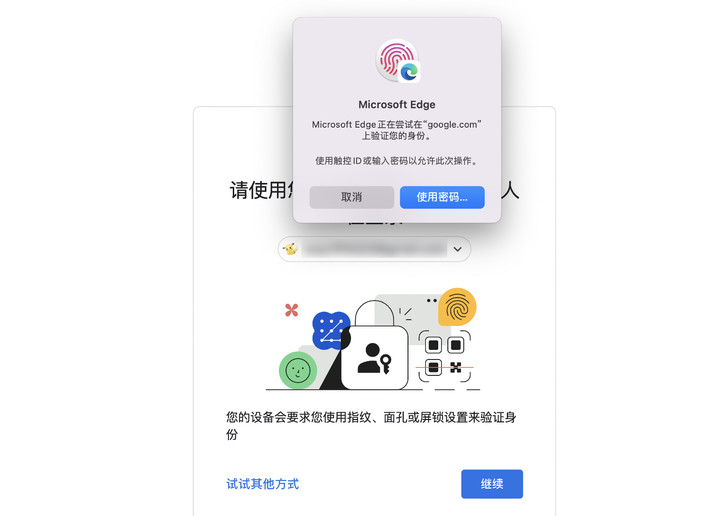
▲ In the certified browser, you can log in through fingerprint verification
Second, Google Passkey is different even when it comes to scanning codes. Scanning and unlocking can only transmit passwords through USB, NFC and Bluetooth, that is to say, you must be near the device when entering the password, otherwise it cannot be verified.
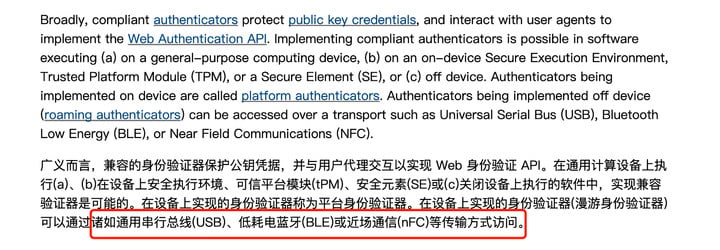
▲ W3C standard
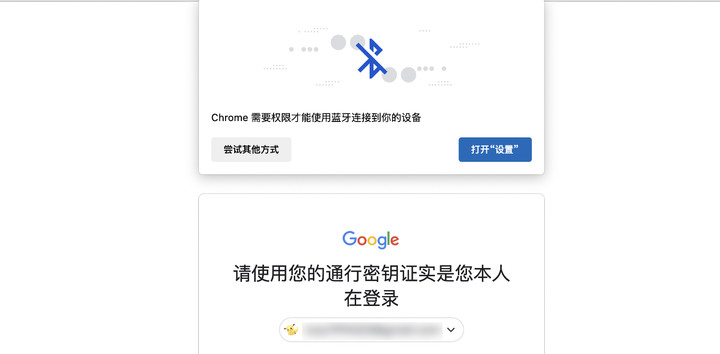
▲ The browser will obtain Bluetooth permission when logging in
To sum it up briefly:
- Google Passkey saves the password locally, completely offline, without server participation, and there is no possibility of the password being intercepted;
- When logging in across devices, it must be at the same location as the login source, eliminating the possibility of scanning codes in different places by mistake.
Google said that most people are more likely to protect their devices than protect their passwords. Even if your device (mobile phone/computer) is lost, you can quickly revoke authorization in the account settings.
Not just Google, as early as 2021, Microsoft allowed users to delete the password of the Microsoft account, and only use fingerprints, faces, Windows Hello, security keys, Microsoft authentication programs, SMS and even email verification codes to log in to Microsoft accounts.
The digital passwords that accompany us into the era of computer networks are leaving us.
From making passwords more complex to making passwords non-existent
Enter the account number and password, click confirm, and enter the website. This common Internet login method unconsciously adds a few more steps: enter the mobile phone verification code, and enter the secondary verification code. This is all to add another layer of security to your password.
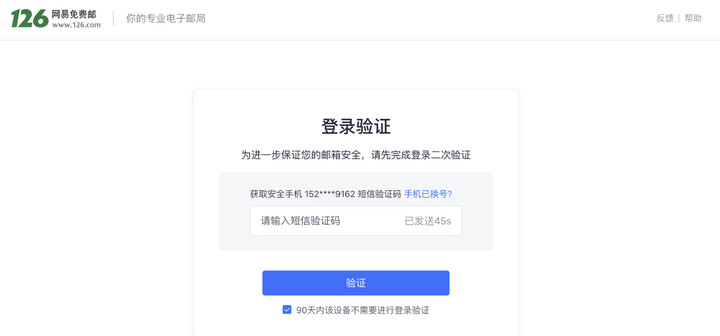
Adding passwords to passwords sounds weird, but as we use more and more network services, we need to remember more and more passwords. In order to reduce the memory cost, password reuse has become a big problem. Once stolen, It will cause a series of personal accounts to lose protection. In order to protect users’ fragile repeated passwords, verification codes and other forms are also a last resort.
Cryptography has become “a kind of nightmare,” Fernando Corbató, the inventor of digital cryptography, said in an interview.
Unfortunately, as the World Wide Web has grown, this has turned into a nightmare. I don’t think anyone can remember all the passwords that are issued or set. That leaves people with two options. You either write down all your passwords in a little notebook, or you choose some kind of software to manage them, but either way is a hassle.

▲ Digital password inventor Fernando Corbató
Before computers were widely used, Fernando Corbató predicted that the Internet and information security systems would be attacked: “The really scary thing is that we have made computers extremely easy to use, so they will be used more and more. This point of view is also applicable to passwords. Passwords are a solution with a very low threshold, so it will also be targeted.
In 2016, Yahoo issued a statement saying that it was hacked, resulting in the leakage of 3 billion user information; in 2022, the password management giant LastPass was hacked twice. Although Lastpass stated that no passwords were stolen, it still sounded the alarm for users.

Bret Arsenault, Microsoft’s chief information security officer, said: Not everyone hates passwords, there are still a small number of people who like passwords, and their names are criminals-although in 2017, Microsoft also said that passwords have a certain ability to stop crime.
Simple passwords are not safe, and complex passwords cannot be remembered. As a security authentication method, passwords have many shortcomings.
In order for us to “remember” the password, the keychain is one of the methods. When you are about to log in to your account on an iPhone or other device, the keychain information will appear above the input method, and you can quickly enter the account password through your fingerprint or face ID.
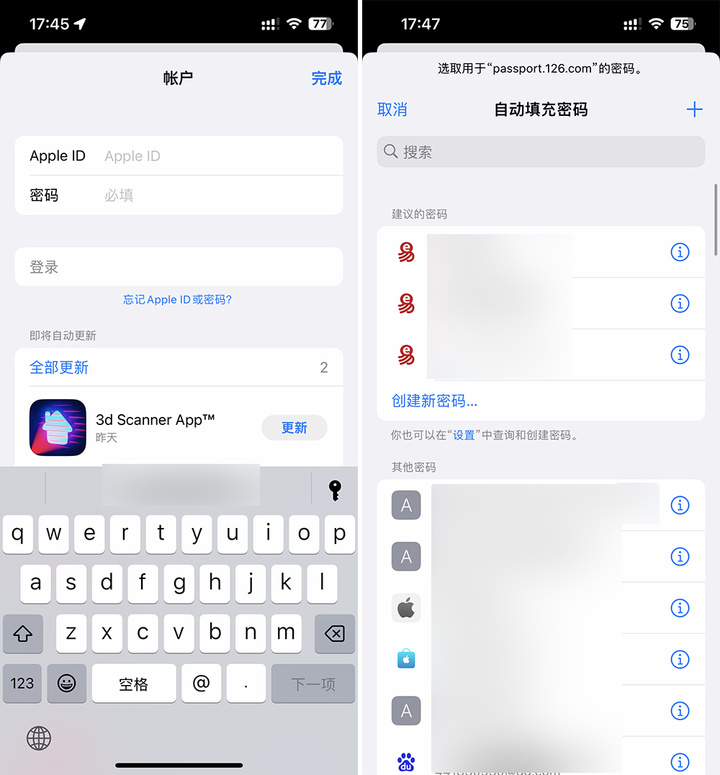
But if your iPhone is lost and the person who finds it happens to guess your unlock password correctly, all the passwords in the keychain will become decorations—if the iPhone does not pass biometric authentication, the lock screen password will be used to unlock the key string.
So I suggest that you do not use a 6-digit password to lock your phone, this is the last line of defense for all your passwords.
As long as the password exists, there is a risk of it being stolen. Perhaps everyone has finally realized this, double verification, software verification, local verification… the ultimate solution to password protection is coming:
Otherwise, let’s give up the password.
In the post-password era, Googles have a long way to go
There are some problems in the existing passwordless schemes.
For example, anyone who knows the lock screen password can log into your Apple ID on your Mac.
Have a lock screen password, which is equivalent to having the Apple ID password in the keychain, and require two-factor authentication when logging in? It doesn’t matter, when the browser logs in to the account, this Mac is the authentication device.
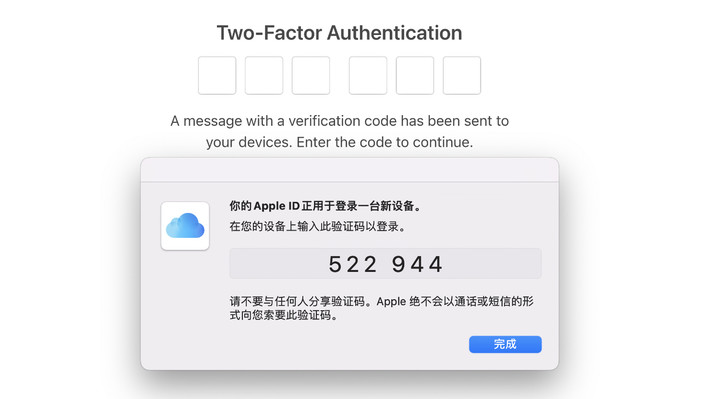
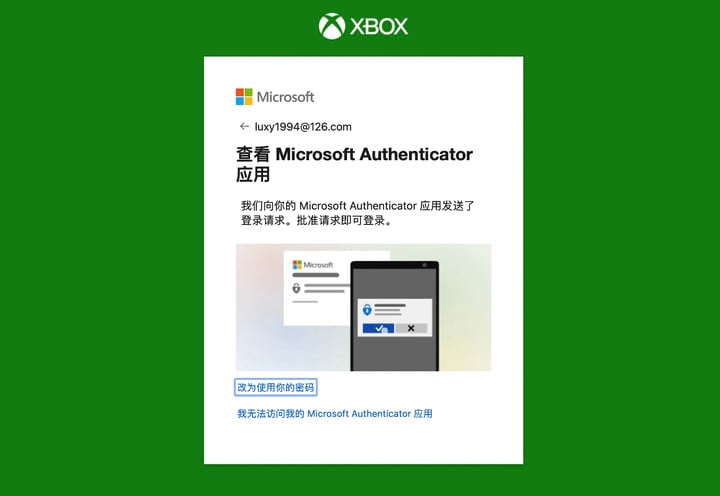
For another example, Microsoft’s Authenticator is very useful as a double verification app. When logging in to a Microsoft account, you need to click on the same numeric code on your phone as the prompt to log in without a password.
Although the situation of one-stop loss of information on the same device when the device is lost is avoided, the risk of logging in from another place after being cheated still exists.
▲ If you encounter a scam, you have been cheated at this time
Google Passkey uses an authorized device (mobile phone) to scan the code at close range to log in to the account to unlock the account, which solves the above two problems to a certain extent, but if the biological “password” is stolen (of course, the possibility is very small), the consequences will be more serious. Seriously, after all, you can change the digital password at will, but your face, fingerprints, and voice cannot be changed. Once stolen, you will worry about it for life. Google Passkey uses an authorized device (mobile phone) to scan the code at close range to log in to the account to unlock the account, which solves the above two problems to a certain extent, but if the biological “password” is stolen (of course, the possibility is very small), the consequences will be more serious. Seriously, after all, you can change the digital password at will, but your face, fingerprints, and voice cannot be changed. Once stolen, you will worry about it for life.
On the other hand, even though manufacturers try hard to make us forget passwords, users do not buy enough of “no password”. The concept that passwords equal security has long been ingrained in users’ minds.
FIDO, an industry association established in July 2012, aims to solve the problem that users face a large number of complex usernames and passwords. Microsoft, Apple, Google, Facebook, etc. are all members of the association.
Its executive director Andrew Shikiar believes that users have long been accustomed to setting passwords, and it is difficult to change user behavior and reduce their dependence on passwords.
Therefore, FIDO’s work is more to popularize the benefits of password-free experience to ordinary users, so that more people can accept the concept that no password is better. This is a bit like quitting smoking. The convenience of passwords is like the pleasure of cigarettes, but its long-term health risks should be understood by more and more people.
In addition to doing science popularization, FIDO will also make suggestions on new password-free technologies to make password-free systems more and more standardized.
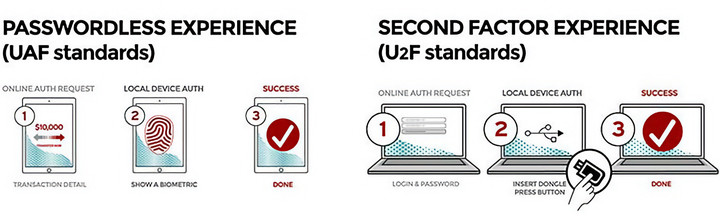
▲ No password and secondary verification legend
Nowadays, there are more and more forms of unlocking using biometric identification such as fingerprints, faces, and voices, and device-assisted login and verification forms are also commonplace.
But even though there are already many ways to log in without passwords, passwords are still not so easy to disappear. The update of old equipment, the change of user concepts, the follow-up of major manufacturers, and the long way to go “no password” still require Google to continue to work hard.
This article is transferred from: https://www.ifanr.com/app/1546279
This site is only for collection, and the copyright belongs to the original author.