Since Weibo and other social platforms launched the IP territorial function, there have been more and more discussions on whether IP display will leak privacy, and some people even choose to spend tens of yuan per month to subscribe to modify the IP territorial service.
IP attribution will reveal privacy, is that true?

▲ Picture from: androidayuda
The answer is no, but there is a risk of privacy leakage in paying to modify the IP attribution.
Modifying the IP attribution is risky
To know what it is, to know if it will, and before we know if an IP leaks privacy, we need to know what it is.
Nowadays, surfing in the ocean of the Internet relies on ubiquitous network links. They are like huge cobwebs linked together. WWW links are the most convenient and intuitive access addresses, connecting Internet platforms such as Weibo.

▲www is an easy-to-remember Internet address prefix. Image from: TechSpot
Such a convenient Internet does not exist in one cluster. Before the invention of the WWW Internet site, communication between computers needed to rely on a specified network transmission protocol, and the IP address was the transmission address.
To realize data communication between your computer and platforms such as Weibo, and realize functions such as publishing pictures and Weibo, you need to clarify the IP addresses of both parties.
There are two types of network transmission protocols, namely IPv4 and IPv6. The former was developed by ARPANET, the predecessor of the Internet, and the latter was supplemented after the IPv4 address was used up.
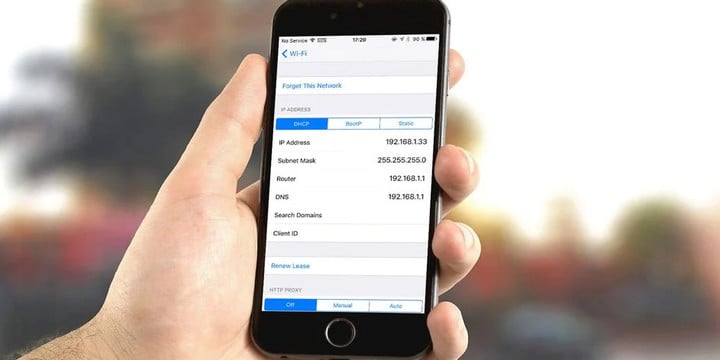
When purchasing broadband services, telecom operators will assign an IP address to them. For example, the IP address of 219.136.162.58 belongs to Baiyun District, Guangzhou City, Guangdong Province.
Even after the URL becomes a common access address, the IP transmission protocol is still retained. Behind the image you send is actually the communication between you and the IP address of the official Weibo server.
This process is not completely public, and social media such as Weibo shows that the IP attribution is only at the provincial (municipal) level, and will not contact your detailed location.
▲ The attribution will be displayed at the end of the APPSO WeChat official account.
Before the arrival of the virtual world like the Metaverse, the IP address in the online world is not uniquely bound to you. After all, the IP address will change. When you go to other provinces and cities to access WiFi in other places, the IP belongs to the ground will change.
If you purchase the corresponding service in order to modify the IP territorial, there is a risk of privacy leakage.
Modifying IP through other services is like adding a “middleman” between you and Weibo and other platforms. You may intercept these data in the process of sending chat messages, pictures, and even payment passwords. Privacy So leaked.
At present, mainstream websites basically use the HTTPS secure transmission protocol, which supports end-to-end encryption, that is, the original plaintext information is stored in a unique ciphertext form, which cannot be “translated” without decrypting it with a specific password.

▲The website address prefix contains the HTTPS prefix, which means that the HTTPS security protocol is supported. Image from: montsepenarroya
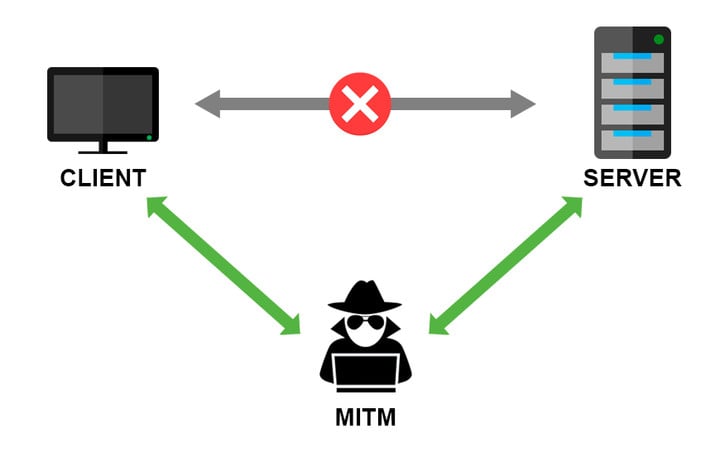
However, end-to-end encryption may also fail. When you purchase an IP modification service, some service providers will require you to install a “system root certificate”.
With this system root certificate, the middleman has the proof, simulates a platform such as Weibo in front of your mobile phone, and obtains the data you send, and in front of platforms such as Weibo, simulates it as your mobile phone to obtain the data sent back.
In this way, the encryption of the communication data between you and the platform is invalid, and the middleman can get the private data, including the private data you send and return.
After the popularity of the app, major companies have proposed new solutions. They no longer trust the system root certificate of mobile phones and other devices, but built a dedicated certificate in the app. Data communication needs to be confirmed by the built-in certificate of the app before decryption.
Network security is a war without gunpowder and will not stop. Encryption and anti-encryption, related technologies are constantly changing and upgrading, and modifying IP services is like handing over your data to a “middleman”, which greatly increases the risk of privacy leakage .
As ordinary people, you and I don’t have to pay for the service of modifying the IP attribution to enter this escalating struggle.
Protecting privacy starts with “valuing” personal data
We have discussed how to protect privacy during daily Internet surfing. For example, before sharing photos on the Internet, we have removed the map location and other shooting information.

▲iPhone album provides editing address function, which can be deleted directly
Compared with the IP attribution, the map location information in the photo is much more accurate.
And try not to compare the “scissor hand” Pose when taking pictures, the white hat hacker Jan Krissler used high-definition finger map to build a high-precision fingerprint, in order to crack the iPhone 5S’s Touch ID sensor.

Prevention technology is constantly improving and upgrading, and now there is a more secure ultrasonic fingerprint technology under the screen. Both Google and Apple attach great importance to mobile phone privacy management and provide many functions.
For example, in the App tracking function on the iPhone, when a new App is opened, the system will pop up a notification, whether to allow data tracking, and choosing No can often reduce the type and amount of personal data that the app tracks you.
The existence of data brokers gives advertisers the opportunity to purchase data from multiple brokers, including positioning data, purchase data, clicks on Internet content, etc., and then establish a detailed user preference profile. Here is the e-commerce One of the reasons why the platform can always recommend “you just searched for a product”.

In this process, the positioning data is one of the most frequently called basic data. If it is not necessary, it is better to turn off the background positioning permission of the application.
On the latest version of the system, both Android and iPhone provide a permission management function. You can view what the application is quietly doing in the background, and you can turn off the permission without related functions. For example, the input method application does not necessarily need the location permission.
Privacy leakage refers not only to your complete personal information, but to items of small and precise data, precise positioning information, and activity information for a certain period of time, which piece together your “personal image”.
To protect privacy, we must start with a concept and reduce the outflow of such personal data in detail.
Finally to sum up:
– IP territorial display is only up to the provincial level and will not reveal privacy
– It is not worth paying to change the IP address, and there is a risk of leaking privacy
– To protect privacy, it is necessary to establish concepts and habits. When the function of privacy protection is used, unnecessary application permissions may not be granted, such as positioning permissions.
This article is reprinted from: https://www.ifanr.com/app/1487600
This site is for inclusion only, and the copyright belongs to the original author.