iKuai routing system, a Linux-based domestic routing system, is characterized by DPI flow control and free, and has certain auditing functions. At present, it seems to be the most commonly used soft routing system in China except OpenWrt.
However, similar to some other dedicated routing systems, iKuai itself is relatively closed, does not open the Linux shell, and even the rootfs is encrypted, which is naturally understandable in business, but the iKuai system was reported to have hijacked the DNS of the user network a few years ago. And the use of HTTP requests for ad monetization, although rumored to have been removed, still raises concerns about its “private goods”.
So this time, I used the iKuai routing system as a secondary router, connected to the RouterOS main router. RouterOS has convenient firewall configuration and packet capture functions. You can set filters to capture packets and save them to a file, and then import them into Wireshark for viewing.
The iKuai system used is “free version 3.6.0 x64 Build202202101800 trial version”, which should be little different from the current 3.5.4 official version in terms of network activity behavior. In iKuai, the “ikuai cloud” and SD-WAN functions are not enabled, only the default automatic update is turned on, which means that ikuai itself should not access any external network except “download.ikuai8.com”.
As of 2022.02, the iKuai system has a link to the privacy policy document on the “Aikuiyun” page, but it only describes the privacy policy of iKuai, and does not explain the iKuai routing system itself without using “Aikuiyun” What information will be uploaded.
DNS packet capture
Intercepting DNS requests is a convenient way to find out which domain names it is trying to access. This time, iKuai is first banned from any connections except “download.ikuai8.com” and 114.114.114.114 DNS, and then intercepted within dozens of minutes of its startup. All DNS requests for:
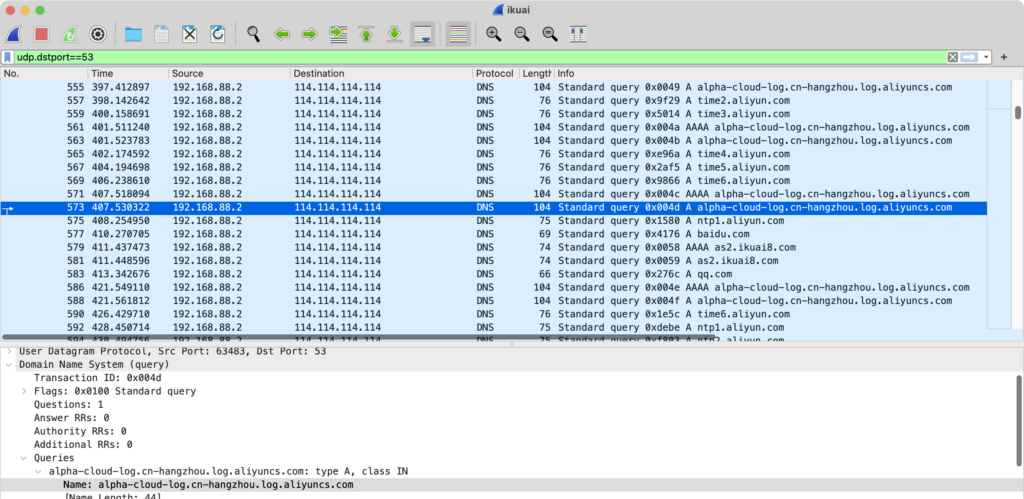
After sorting, all the domain names queried are as follows:
NTP服务,正常行为: 0.centos.pool.ntp.org 1.centos.pool.ntp.org 2.centos.pool.ntp.org ntp.aliyun.com软件更新,正常行为: download.ikuai8.com意义不明的名字,但IP与download.ikuai8.com相同: 302.ikuai8.com爱快云: yun.ikuai8.com.w.kunlungr.com (CNAME自yun.ikuai8.com)疑似使用情况上报,存在疑问(如:上传了哪些信息?): report.ikuai8.com.w.kunluncan.com (CNAME自report.ikuai8.com)阿里云-日志服务SLS,存在疑问(如:上传了哪些信息?): alpha-cloud-log.cn-hangzhou.log.aliyuncs.com疑似阿里广告服务(友盟),存在疑问: secgw-na61-na62.wagbridge.alibaba.alibabacorp.com (CNAME自umdc.aliapp.org)用途未知,存在疑问,对应IP都属于阿里的AS37963: as1.ikuai8.com as2.ikuai8.com dis.ikuai8.com pkgmanager.ikuai8.com江苏电信的IP,疑似用于宽带加速服务,存在疑问: fastgame.ikuai8.com可能用于网络检测: baidu.com qq.com
Note: The above is the domain name query and personal subjective speculation collected by a single simple experiment, and we are not responsible for its correctness and do not make any evaluation. If the official or third party can provide more information, please leave a message in the comment area.
The rules used in the upper-level routing are as follows (192.168.88.2 is the IP of iKuai):
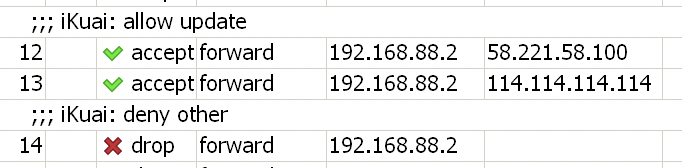
To be continued, and when you have time, prepare for a full-day packet capture.
This article is reprinted from: https://wusiyu.me/2022%E5%B9%B4%EF%BC%8C%E5%AF%B9%E4%BA%8E%E7%88%B1%E5%BF%AB%EF %BC%88ikuai%EF%BC%89%E8%B7%AF%E7%94%B1%E7%B3%BB%E7%BB%9F%E6%9C%AC%E8%BA%AB%E7%BD %91%E7%BB%9C%E6%B4%BB%E5%8A%A8%E7%9A%84%E7%AE%80%E5%8D%95/
This site is for inclusion only, and the copyright belongs to the original author.